History
-

Advanced Network Reconnaissance with Nmap
Video This video is a presentation by Gordoon Lyon aka Fydor, the creator of the nmap network scanner, from ShmooCon 2006. From...
-

After Modernity: Archaeological Approaches to the Contemporary Past
Book The introduction to this book provides access to the debate on the "archeology of the contemporary" or, in other terms, the archeology of...
-

An Evening with Berferd: In Which a Cracker is Lured, Endured, and Studied
Article This article is written by Bell Labs researcher Bill Cheswick about Unix security. Cheswick studied a hacker in the wild using an early...
-
A Prehistory of Social Media
Article This article provides an introduction to the birth of social media by providing a "prehistory" of the internet itself. The article focuses...
-

Back Orifice
Digital Artifact This article details the digital artifact Back Orifice (a play on Windows Back Office) created by the hacking group Cult of the...
-

BBS The Documentary: Episode 1 of 8: BAUD (The Beginning)
Video This video is episode 1 of 8 of a documentary mini-series by Jason Scott about the bulletin board systems (BBS). From...
-

Book Launch: The Hacker and the State
Video This video is the book launch of Dr. Ben Buchanan's book The Hacker and the State. From the video description, "Packed with...
-

Countdown to Zero Day: Stuxnet and the Launch of the World's First Digital Weapon
Book This book describes the details of the history and technological development of the Stuxnet Worm. Kim Zetter is a top cybersecurity journalist...
-

Cult of the Dead Cow
Book Chapter This book chapter from the recent book on the hacking group the Cult of the Dead Cow is about the Back Orifice...
-

DEF CON 19 - Jason Scott - Archive Team: A Distributed Preservation of Service Attack
Video This video depicts a presentation by Jason Scott at the hacker conference, DEFCON '19 about the preservation of digital artifacts on...
-

DEFCON - The Full Documentary
Video This video is a documentary of the DefCon hacker conference and hacking convention. From the video description, "A film about the world's...
-

Digital Archaeology: Rescuing Neglected and Damaged Data Resources
Academic Paper This article from the University of Glasgow is a handy guide for historical preservation in the 1990s that makes use of...
-

Digital Equipment Corporation PDP-11
Digital Artifact This article details the history and technical developments of the PDP-11, a series of 16-bit microcomputers sold by Digital Equipment Corporation...
-

Exploding the Phone
Book This book provides an in-depth historical perspective and study of phone phreaking and hackers of the telecommunication industry known as phone...
-

Freedom Downtime
Video This video is the documentary from 2001 that is sympathetic to convicted computer hacker, Kevin Mitnick. It is produced by 2600...
-

From Internet Farming to Weapons of the Geek
Article This article details the history of political hacking by Gabriella Coleman in which she provides an introduction and inventory of the...
-

Hacker Crackdown: Law and Disorder on the Electronic Frontier
Book Chapter This book details the spirit of the times with the criminalization (and eventual crackdown) of the so-called "hacker underground." This particular...
-

Hackers: Heroes of the Computer Revolution
Book Steven Levy's book is is a classic text on the history of computing. It is used throughout the course to highlight the hacker...
-

Hackers Testimony at the United States Senate
Video This video depicts the testimony of the hacker group, L0pht Heavy Industries, in front of the United States Senate in 1998. The...
-

How the Apple-1 Works
Video This video provides a technical overview of the Apple-1 Computer. The technical aspects of the computer are described and shown as...
-

Masters of Crowds: The Rise of Mass Social Engineering
Article This article provides a deep history of mass manipulation from the 1920s through the mid-1970s. This article is adapted from the...
-
Operation Sundevil
Video The video provides a brief overview of Operation Sundevil from the 1990s. The operation was apart of a large hacker crackdown...
-

Phone Phreaking: A Call From Joybubbles
Video This video depicts a phone phreaking call made by the hacker Joybubbles aka Josef Engressia, Jr. This original sound byte comes...
-

Phrack Magazine - Issue 31
Article This article is an introduction to Issue 31 of the popular underground hacking publication of Phrack Magazine. This particular article details...
-

Red Box (Phreaking)
Article This article provides a technical description and history of the red box phone phreaking device. This device was created and utilized...
-

Reflections on Trusting Trust
Article This article is a written version of an Alan Turing Award Lecture from Ken Thomson in 1984. This article is a...
-

Remote OS detection via TCP/IP Stack FingerPrinting
Article This article is from issuse 54 of Phrack Magazine in 1998 written by Gordon Lyon aka Fydor, the creator of the...
-

Rene Carmille
Article This article details the life of Rene Carmille who is known to be one of the first hackers. This article gives a...
-

Representing Hacker Culture: Reading Phrack
Book Chapter This book chapter from Douglas Thomas' book Hacker Culture details an outsider's guide to reading the hacker zine Phrack. This chapter discusses...
-

Resistance to the current: the dialectics of hacking
Book Chapter This book chapter is titled "Internet Relay Chat: A Time Machine That Stood the Test of Time" and details the history...
-

Smashing the Stack for Fun and Profit
Article This article is from issue 49 of Phrack Magazine written by Elias Levy who also goes by the handle Aleph One in...
-
Spacewar!
Digital Artifact This game is a digital artifact of a Javascript version of the popular Spacewar! video game that is one of the...
-
Stalking the Wily Hacker
Article This article tells the story of a hacker who penetrated Lawrence Berkeley National Laboratory in the 1980s. It provides an anecdotal perspective...
-

Storage Media
Article This article provides the technical developments of various data storage methods and mediums throughout history. These digital artifacts provide an understanding...
-

The Art of Deception
Book This book is a digital artifact used in the course to represent the area of social engineering. The book details several...
-

The Art of Port Scanning
Article This article from issue 51 of Phrack Magazine is written by Gordon Lyon aka Fydor about the nmap network scanner. This article introduced...
-

The First Hacker
Video This video gives an overview of Rene Carmille's contribution as the first hacker. From the video description: "Based on the extraordinary...
-

The Government's Fight to Make Encryption Illegal
Video This video is the third-part of a four part documentary by ReasonTV titled "Cypherpunks Write Code". From the video description: In 1977,...
-

The Hacker Conference: A Ritual Condensation and Celebration of a Lifeworld
Academic Paper This paper written by Gabriella Coleman, anthropologist and expert on all things computer hacking, provides a new scholarly perspective on hacker conferences....
-
The Secret History of Hacking
Video This video depicts some of the secret side of the history of hacking from black hat hackers to white hat hackers....
-

Unauthorized Access
Video This video is a documentary about hackers by Annalisa Savage from 1994. From the video description, "This is a nostalgic hacker documentary...
-
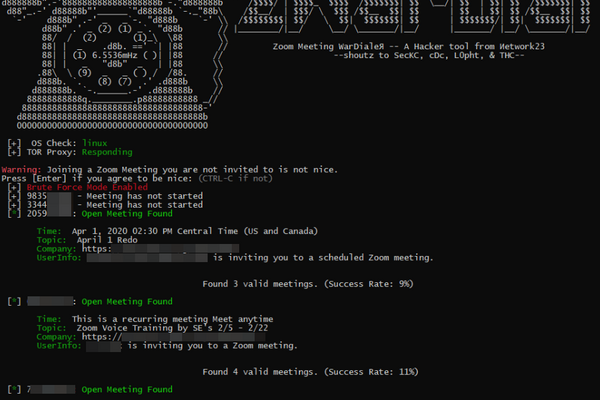
War Dialer
Digital Artifact This article provides historical context and the technical developments in wardialing and war dialers. War dialing is a technique developed by hackers...
-

Warez: The Infrastructure and Aesthetics of Piracy
Book This book is written by Martin Paul Eve, a Professor of Literature, Technology and Publishing, about the Warez Scene and community. This...
-
Watch Me Demo My New IRC Client on an 80s Retro Computer
Video This video is a video of a demo of Internet Relay Chat (IRC) on an 80s retro computer. The IRC is highly...