Resources
-

3 cyber mercenaries: An insider threat case study
Article This article tells the story of three US nationals who assisted the United Arab Emirates in exploiting Apple's operating system and...
-

6 Links That Will Show You What Google Knows About You
Article In this article, there are 6 links featured that, when clicked, give you a peek into the data Google has...
-
ACM Code of Ethics and Professional Conduct
Other This code of ethics put forth by the Association for Computing Machinery seeks to guide the ethical conduct of computing professionals.
-

Action versus Contemplation
Book The description for this book is as follows: "'All of humanity’s problems stem from man’s inability to sit quietly in a room alone,' Blaise...
-
Adblocking: How About Nah?
Article In this article, the author discusses the ethics of using an ad blocker, and highlighting the position that ad blockers give users...
-

Advanced Network Reconnaissance with Nmap
Video This video is a presentation by Gordoon Lyon aka Fydor, the creator of the nmap network scanner, from ShmooCon 2006. From...
-

Advertising is a cancer on society
Article In this article, the author argues that modern advertising is similar to how cancer takes over the human body. After...
-
A face-scanning algorithm increasingly decides whether you deserve the job
Article This article discusses HireVue, a technology that uses artificial intelligence to analyze job candidates. The article discusses both favorable and unfavorable...
-

A Framework for Making Ethical Decisions
Article In this article, from Brown University's Science and Technology Studies department, the author provides an introduction to making ethical decisions....
-

After Modernity: Archaeological Approaches to the Contemporary Past
Book The introduction to this book provides access to the debate on the "archeology of the contemporary" or, in other terms, the archeology of...
-

After Working at Google, I'll Never Let Myself Love a Job Again
Article In this article, Emi Nietfeld describes what happened to her at Google, a company she once loved.
-

A horrifying new AI app swaps women into porn videos with a click
Article This article describes a website that creates pornography deepfakes. A deepfake is hyper-realistic fake audio or video content depicting something...
-

AI emotion-detection software tested on Uyghurs
Article This article describes how a Chinese software company tested their emotion recognition software on the Uyghurs, a marginalized ethnic group in...
-

AI-Generated Art Scene Explodes as Hackers Create Groundbreaking New Tools
Article This article describes how hackers combined different open source AI tools to create a visual art generator that creates an...
-

AI is increasingly being used to identify emotions – here’s what’s at stake
Article This article discusses some of the issues with Emotion Recognition Technology (ERT). ERT stands on shaky scientific ground and is prone...
-

Airbnb Was Like a Family, Until the Layoffs Started
Article In this article, Erin Griffith depicts the conflict that occurred when Airbnb's company culture faced the realities of the global...
-

Alexa, Should We Trust You?
Article This article discusses the potential of voice assistants like Alexa, Siri, and Google Assistant to change our society. A big...
-

All Tesla Cars Being Produced Now Have Full Self-Driving Hardware
Article This 2016 blog post from Tesla's blog describes how all Tesla cars being produced from that point onward have full self-driving...
-

Amazon cloud sputters for hours, and a boatload of websites go offline
Article In this article, Brodkin reports on the IoT devices that went down during Amazon S3 outage.
-

American Spies: how we got to mass surveillance without even trying
Article This article is a book review of American Spies by Jennifer Stisa Granick. It describes the legal complications surrounding Internet privacy in the United...
-
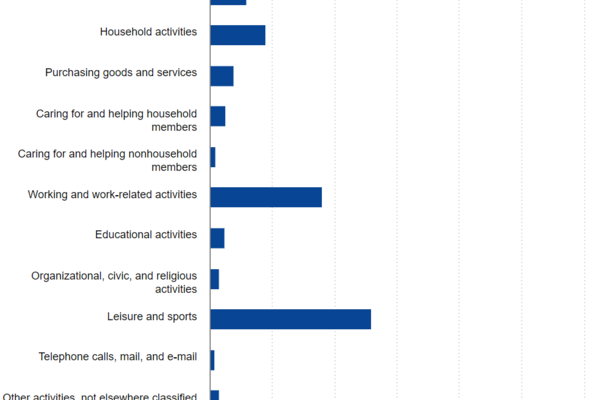
American Time Use Survey
Report Summary: In this report, the US Bureau of Labor Statistics details how Americans spend their time. There are many data...
-

A Message To Our Customers
Article This letter from Apple to its customers explains why Apple refused to comply with the FBI's request for a "backdoor" to...
-
An anonymous response to dangerous FOSS Codes of Conduct
Article In this article, an anonymous writer pens a response to what he believes are Dangerous FOSS Codes of Conduct. He argues the...
-

Andrew Yang Is Full of It
Article In this article, the author pushes back against Andrew Yang's dystopian warnings about automation and mass unemployment that have motivated...
-

An Evening with Berferd: In Which a Cracker is Lured, Endured, and Studied
Article This article is written by Bell Labs researcher Bill Cheswick about Unix security. Cheswick studied a hacker in the wild using an early...
-

A New Harassment Policy for Twitter
Article This article describes Twitter's 2014 response to targeted harassment on their site. This response included an easier way for users to manage...
-

An Oral History of the L0pht
Article This series of articles is an oral history of one of the more influential hacker groups, the Boston-based hacker group,...
-
A Novice's Guide to Hacking- 1989 edition
Article This article is a classic piece of self-directed training in hacking by a hacker with the handle The Mentor from the...
-

A Philosopher Looks at Work
Book The description for this book is as follows: "Is work as we know it disappearing? And if so why should we...
-

A philosopher’s view: the benefits and dignity of work
Article In this article, Image Credit: Rafael Cavalcante/Flickr
-

Apple, Facebook, Google, Amazon Top Interviewer Reveals Secrets of Landing Dream Job
Article In this article, one of Silicon Valley's top interviewers tells all about how to win a highly coveted job at the...
-

Apple, Google will pay 64,000 engineers to avoid trial on “no-poach” deal
Article In this article, Joe Mullin talks about a class-action lawsuit against Google, Apple, Adobe, and Intel over how they recruited employees which was...
-

Apple I
Digital Artifact This article details the technical development and contextual history of the Apple I, originally released under the name Apple Computer. This...
-

A Preface To Economic Democracy
Book In this book, Dahl explores the notions of liberty and equality, and argues that, contrary to Tocqueville's claim, the two...
-
A Prehistory of Social Media
Article This article provides an introduction to the birth of social media by providing a "prehistory" of the internet itself. The article focuses...
-

A Radical Cure: Hannah Arendt & Simone Weil on the Need for Roots
Article In this article, Remer draws on the philosophies of Hannah Arendt and Simone Weil to argue that the modern world...
-

Archaeology of Hacking: Textfiles Explainer
Video This video an overview of the hacker underground media sharing platform known as textfiles.
-

Are Hacker Break-Ins Ethical?
Article From the article description: Eugene H. Spafford argues that we should judge the actions of hackers, not the rationalizations they...
-

Are These the Hidden Deepfakes in the Anthony Bourdain Movie?
Article This article describes the controversy surrounding the use of deepfake audio clips in Roadrunner, a documentary about Anthony Bourdain made after his...
-

Aristotle and Aquinas on the Active and Contemplative Life
Video In this video, Rev. John I. Jenkins, C.S.C., President of the University of Notre Dame, and Dr. Meghan Sullivan (Rev. John...
-

Aristotle: In Praise of Contemplation
Article In this article, the author explains Aristotle's belief that a good life is committed to contemplation. Barrientos shows that Aristotle...
-

Aristotle & Virtue Theory: Crash Course Philosophy #38
Video From the video description: "This week we explore final ethical theory in this unit: Aristotle’s virtue theory. Hank explains the...
-

As Cameras Track Detroit’s Residents, a Debate Ensues Over Racial Bias
Article This article discusses the city of Detroit’s “Project Green Light” initiative which uses facial recognition surveillance to find criminals. Some...
-

Ask HN: How much do you make at Amazon?
Other In this forum, software engineers share how much they make at Amazon.
-

Ask HN: How much do you make at Google?
Other In this forum, software engineers share how much they make at google.
-

A Stoic Guide To Workplace Peace Of Mind
Other In this article, the author gives practical advice, backed by famous stoic philosophers, for how to find peace of mind...
-

Attack of the Anons Lecture Slides
Lecture / slides Slides for Lecture 13 of Ethical and Professional Issues in Notre Dame's Computer Science and Engineering department. The learning goals...
-

Authentic Happiness
Book The description for this book is as follows: "According to esteemed psychologist and bestselling author Martin Seligman, happiness is not...
-
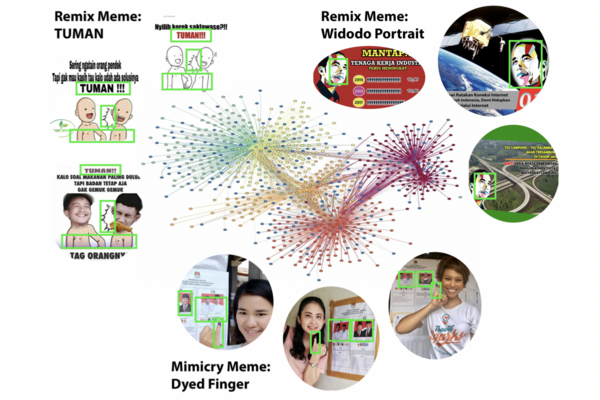
Automatic Discovery of Meme Genres with Diverse Appearances
Academic Paper This academic paper has the following abstract: Forms of human communication are not static — we expect some evolution in...
-

A Vulnerable Internet Lecture Slides
Lecture / slides Slides for Lecture 24 of Ethical and Professional Issues in Notre Dame's Computer Science and Engineering department. The learning goals for...
-

Back Orifice
Digital Artifact This article details the digital artifact Back Orifice (a play on Windows Back Office) created by the hacking group Cult of the...
-

Barr says the US needs encryption backdoors to prevent “going dark.” Um, what?
Article This article discusses a 2019 keynote address by Attorney General William Barr in which he argued that information security "should not...
-

BBS The Documentary: Episode 1 of 8: BAUD (The Beginning)
Video This video is episode 1 of 8 of a documentary mini-series by Jason Scott about the bulletin board systems (BBS). From...
-

Being More Educated May not Make you More Satisfied with Your Job, Study Finds
Article In this article, it presents some interesting findings about education and job satisfaction. It finds, that you might wind up...
-

Being rich wrecks your soul. We used to know that.
Article In this article, the authors use psychology and philosophy to argue that being wealthy is not healthy or good for...
-

Benedictine College Raises the Bar in Fight Against Porn Addiction
Article This article describes Benedictine College’s efforts to discourage pornography viewing on campus. Not only did the Catholic college block pornography...
-

Bernard Williams Thought Experiment (Clip from "Utilitarianism: Crash Course")
Video In this video, Crash Course explains the basics of utilitarian philosophy, which is centered around the idea that the morally...
-
Better, Stronger, Faster
Other This text file from the Cult of the Dead Cow describes the NBC Dateline episode that featured the mysterious hacker "Quentin"...
-

Big Data Business Plan Lecture Slides
Lecture / slides In these lecture slides for the Ethical and Professional Issues course in Notre Dame's Computer Science and Engineering department, the following...
-

Blaschko on the Active vs Contemplative Work Life
Video In this video, Paul Blaschko looks at how thinking about our work lives in terms of the "active vs. contemplative" debate...
-

Boeing Employee Fired for Discussing Computer Security Problems at Company
Article This article tells the story of how Boeing fired an employee for speaking to the Seattle Post-Intelligencer about security issues at...
-

Book Launch: The Hacker and the State
Video This video is the book launch of Dr. Ben Buchanan's book The Hacker and the State. From the video description, "Packed with...
-

Bradley Manning’s Army of One
Article This article tells the story of Chelsea Manning (formerly Bradley Manning). The article tells Manning's life story and how that led...
-

Bridges, Software Engineering, and God
Article In this article, the author describes why software engineering is different from other forms of engineering. The author claims that...
-
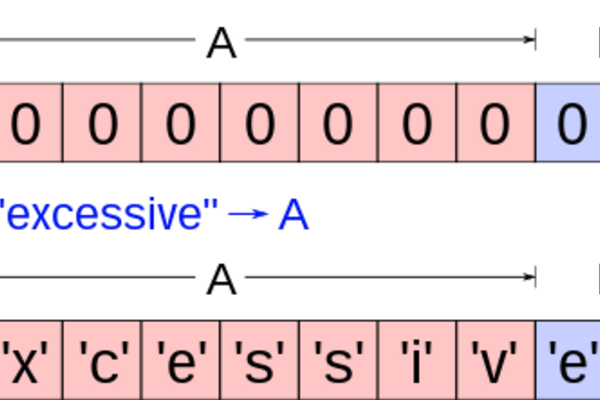
Buffer Overflow Exploit
Digital Artifact This article describes the digital artifact of a buffer overflow exploit. A buffer overflow is an anomaly where a program writes...
-

Building A Better Future Lecture Slides
Lecture / slides Slides for Lecture 26 of Ethical and Professional Issues in Notre Dame's Computer Science and Engineering department. The learning goals for...
-

Bullshit Jobs: A Theory
Book In this book, anthropologist David Graeber argues that millions of people today find themselves in jobs that contribute nothing of...
-

Cancel Culture Lecture Slides
Lecture / slides Slides for Lecture 17 of Ethical and Professional Issues in Notre Dame's Computer Science and Engineering department. The learning goals...
-

Capital One Data Breach Compromises Data of Over 100 Million
Article This article sheds light on a 2019 data breach of data from Capital One bank. The article explains how the suspect,...
-

Car makers can’t “drive their way to safety” with self-driving cars
Article In this article, the author argues that while autonomous vehicles are being promoted in the name of road safety, it...
-

Catholic Officials on Edge After Reports of Priests Using Grindr
Article This article describes the reports of Catholic clergy using the hookup app Grindr by the conservative Catholic blog The Pillar. Editors...
-

Catholic Social Teaching in 3 Minutes
Video In this video, Trócaire explains the basics of Catholic Social Teaching (CST). The central tenets of CST are: Respect for Human Life...
-

Cesare Lombroso
Academic Paper This academic paper has the following abstract: The Italian physician Cesare Lombroso, one of the first scientific criminologists and a forensic psychiatrist,...
-

Changes to Facebook’s "Real Names" Policy Still Don’t Fix the Problem
Article In this article, the authors discuss changes Facebook made to its "real names policy." The real names policy required Facebook users...
-
Change the World, cDc Style
Video This video is from the DefCon 27 Conference and is a presentation by the hacking group Cult of the Dead Cow. This...
-
Chapter 1 - Engineering Ethics
Book This book is an introductory textbook that explores many of the ethical issues that a practicing engineer might encounter in the...
-

China Presses Its Internet Censorship Efforts Across the Globe
Article This article describes the great lengths China goes to in order to censor anti-China content online. While it is well-known that...
-

China says terrorism, fake news impel greater global internet curbs
Article This article describes how China used terrorism and fake news threats as reasons to tighten their national Internet censorship. China likened...
-

China’s Global Reach: Surveillance and Censorship Beyond the Great Firewall
Article This article describes the ways China is able to influence Internet censorship not just domestically but also worldwide. China is able...
-

Cities Have Taken the Lead in Regulating Driverless Vehicles
Article This article describes how cities, rather than federal or state governments, have taken the lead on autonomous vehicle regulation. The article...
-

Cities Need to Take the Wheel in Our Driverless Future
Article In this article, the author argues that cities need to play an active and thoughtful role in regulating the introduction...
-

Clearview AI finally takes part in a federal accuracy test
Article This article describes how the controversial facial recognition algorithm from Clearview AI was put to a third party test for...
-

Coding Freedom: The Ethics and Aesthetics of Hacking
Book This book was written by scholar Gabriella Coleman about the ethics and history of the hacking community. The particular chapter read...
-

Companies Say Trump is Hurting Business By Limiting Legal Immigration
Article This article explores some of the downsides of limiting legal immigration. The article profiles business owners and managers in a variety...
-

Computer security faults put Boeing at risk
Article This article is the article through which a Boeing whistleblower exposed Boeing's internal security risks. Through interviewing Boeing employees and reviewing...
-
CONFidence 2021: The Coming AI Hackers
Video This video is from CONfidence 2021 from Bruce Schneier discussing the future of hacking. From the video description, "Hacking is a human endeavor,...
-

Consolidation in the Internet Economy
Article In this article, answer "How will consolidation impact the Internet’s technical evolution and use?"
-

Contributor Covenant
Other This code of ethics outlines standards of behavior for people contributing to open source projects and participating in open source communities.
-

Countdown to Zero Day: Stuxnet and the Launch of the World's First Digital Weapon
Book This book describes the details of the history and technological development of the Stuxnet Worm. Kim Zetter is a top cybersecurity journalist...
-

Counterproductive: Time Management in the Knowledge Economy
Book In this book, Melissa Gregg argues that the emphasis on productivity as the ultimate measure of job performance is a...
-

Credit reporting firm Equifax says data breach could potentially affect 143 million US consumers
Article This article describes a 2017 data breach affecting Equifax, a company providing credit information. The breach potentially affected 143 million consumers...
-

Crypto
Book Chapter This book chapter is from Steven Levy's book "Crypto" which tells the stories of key figures behind cryptography and the cypherpunk movement. This...
-

Cult of the Dead Cow
Book Chapter This book chapter from the recent book on the hacking group the Cult of the Dead Cow is about the Back Orifice...
-

Cyberbullying in the workplace: 'I became paranoid'
Article In this article, two instances of workplace cyberbullying are profiled. The article notes that the blurred line between work life...
-

Cyberbullying: what it is and how to avoid it
Article This article on cyberbullying describes what it is, its effects, how parents can talk about cyberbullying with their children, and practical tips...
-

Darknet Diaries Ep: 45 Xbox Underground
Video This video details one of the biggest hacks on the Xbox gaming console. From the video description, "It started as a...
-
Dateline on Computer Hacking
Video In this NBC Dateline episode from 1992, the hosts expose how hackers are easily able to break into the computer systems...
-

David Foster Wallace discusses Consumerism
Video In this video, David Foster Wallace discusses the dangers of consumerism and teaching individualistic self-gratification to children. He argues that...
-

Dear Silicon Valley: America’s fallen out of love with you
Article In this article, the author tells Silicon Valley that America has fallen out of love with it. The author lists...
-
Deepfakes Are Now Making Business Pitches
Article This article describes how deepfakes--hyper-realistic fake videos--are making their way into the business world. Specifically, the article profiles how EY uses...
-

Deepfake satellite imagery poses a not-so-distant threat, warn geographers
Article This article describes the threat of geographic deepfakes. Most people think of deepfakes as hyper-realistic fake videos of people saying...
-

Deepfakes in cyberattacks aren’t coming. They’re already here.
Article This article outlines some of the concerns about deepfakes—hyper-realistic fake videos created with artificial intelligence. The concerns listed in the...
-

Deep Work
Book The description for this book is as follows: "Deep work is the ability to focus without distraction on a cognitively...
-

DEF CON 19 - Jason Scott - Archive Team: A Distributed Preservation of Service Attack
Video This video depicts a presentation by Jason Scott at the hacker conference, DEFCON '19 about the preservation of digital artifacts on...
-

DEFCON - The Full Documentary
Video This video is a documentary of the DefCon hacker conference and hacking convention. From the video description, "A film about the world's...
-
Defund Facial Recognition
Article This article describes how facial recognition in policing is a particular threat to Black lives and to democracy. The article...
-

Designed to Deceive: Do These People Look Real to You?
Article This article describes how machine learning algorithms (specifically Generative Adversarial Networks or GANs) are able to create incredibly realistic-looking human...
-

Dialectic of Enlightenment
The description for this book is as follows: "Dialectic of Enlightenment is undoubtedly the most influential publication of the Frankfurt School...
-

Dialogue Group 1
Dialogue Group This dialogue group meeting prompt was used in the Ethical and Professional Issues Course in Notre Dame's Computer Science and...
-

Dialogue Group 10
Dialogue Group This dialogue group meeting prompt was used in the Ethical and Professional Issues Course in Notre Dame's Computer Science and...
-

Dialogue Group 11
Dialogue Group This dialogue group meeting prompt was used in the Ethical and Professional Issues Course in Notre Dame's Computer Science and...
-

Dialogue Group 2
Dialogue Group This dialogue group meeting prompt was used in the Ethical and Professional Issues Course in Notre Dame's Computer Science and...
-

Dialogue Group 3
Dialogue Group This dialogue group meeting prompt was used in the Ethical and Professional Issues Course in Notre Dame's Computer Science and...
-
Dialogue Group 4
Dialogue Group This dialogue group meeting prompt was used in the Ethical and Professional Issues Course in Notre Dame's Computer Science and...
-

Dialogue Group 5
Dialogue Group This dialogue group meeting prompt was used in the Ethical and Professional Issues Course in Notre Dame's Computer Science and...
-

Dialogue Group 6
Dialogue Group This dialogue group meeting prompt was used in the Ethical and Professional Issues Course in Notre Dame's Computer Science and...
-

Dialogue Group 7
Dialogue Group This dialogue group meeting prompt was used in the Ethical and Professional Issues Course in Notre Dame's Computer Science and...
-
Dialogue Group 8
Dialogue Group This dialogue group meeting prompt was used in the Ethical and Professional Issues Course in Notre Dame's Computer Science and...
-

Dialogue Group 9
Dialogue Group This dialogue group meeting prompt was used in the Ethical and Professional Issues Course in Notre Dame's Computer Science and...
-

Dialogue Group Meeting 0
Dialogue Group This dialogue group meeting prompt was used in the Ethical and Professional Issues Course in Notre Dame's Computer Science and...
-
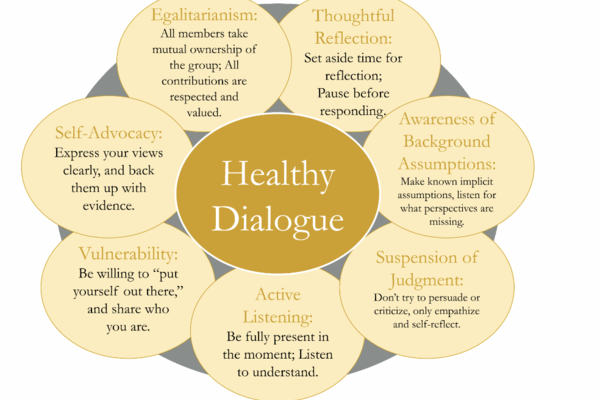
Dialogue Training Manual
Dialogue Group In everyday life, a “dialogue” is any conversation in which all participants share perspectives on a question or idea and...
-

Digital Archaeology: Rescuing Neglected and Damaged Data Resources
Academic Paper This article from the University of Glasgow is a handy guide for historical preservation in the 1990s that makes use of...
-

Digital Equipment Corporation PDP-11
Digital Artifact This article details the history and technical developments of the PDP-11, a series of 16-bit microcomputers sold by Digital Equipment Corporation...
-
Disinformation
Video In this video from the 1990s, members of the hacking group the Cult of the Dead Cow comment on where they...
-

Don't Give Silicon Valley More H1B Visas
Article In this article, the author argues again giving Silicon Valley more H1B Visas. The author argues that the H1B Visa...
-

Drive
Book The description for this book is as follows: "Most people believe that the best way to motivate is with rewards...
-

Ecclesiastes Chapter 1 (from the Bible)
Poem In the opening chapter of Ecclesiastes, a speaker who identifies themself as a preacher and king of Jerusalem proclaim a deeply nihilistic...
-

Economic Inequality
Article In this article, Graham sheds light on the roots of economic inequality.
-

Edmonton gore site owner charged in Magnotta video investigation released on bail
Article This article describes the legal action taken towards Mark Marek, the owner of the website bestgore.com that hosted a video...
-

Edward Snowden, the media, and the Espionage Act
Article In this article, the author argues that Edward Snowden should not be pardoned. The author argues that Snowden's intention was...
-

Emotion AI researchers say overblown claims give their work a bad name
Article This article discusses emotion recognition, the technology used by HireVue to screen job candidates using artificial intelligence. The article discusses the limitations...
-
Employees Who Stay In Companies Longer Than Two Years Get Paid 50% Less
Article In this article, Cameron Keng provides evidence that staying employed at the same company for over two years on average is...
-

Engineers Are Leaving Trump’s America for the Canadian Dream
Article This article highlights the stories of former United States H-1B workers who moved to Canada because of its more welcoming immigration policy. It...
-

Ethical and Professional Issues Trailer
Video From the video description: "Prof. Walter Scheirer (Computer Science, University of Notre Dame) introduces his new course, 'Ethical and Professional...
-

Ethical Decision Making
Video In this video, you are asked to think about the last time you made a big decision. Why did you...
-

Ethics and the Second Law of Thermodynamics
Article In this article, the author discusses the reality that many engineers who have gotten into trouble because of ethical violations...
-

Ethics Defined: Integrity
Video In this video, the McCombs School of Business looks to define integrity. Integrity is an essential moral virtue that is the...
-

Ethics in the Conflicts of Modernity
Book The description for this book is as follows: "Alasdair MacIntyre explores some central philosophical, political and moral claims of modernity...
-

Europe Wants to Ban Facial Recognition—Take Note, America
Article This article discusses how the European Parliament has called on EU lawmakers to ban biometric surveillance in public spaces. Members...
-

'Every smile you fake' — an AI emotion-recognition system can assess how 'happy' China's workers are in the office
Article In this article, a Chinese emotion recognition system is described. The developers of this technology claim that their system can...
-

“Everything as a service” is coming—but we’re not there quite yet
Article This article discusses some of the challenges in moving towards cloud computing as a service. One issue mentioned is privacy and...
-

Everything is GamerGate
Article This compilation of reflections places the GamerGate campaign in context with other current events. GamerGate was an online harassment campaign targeted initially at...
-

Excellence in opera or saving a life? Your choice.
Article In this article, Peter Singer questions where one ought to direct their charitable donations. For example, does donating to prevent...
-

Exclusive: Here's The Full 10-Page Anti-Diversity Screed Circulating Internally at Google
Article In this article, a now infamous memo from a male Google employee (James Damore), titled “Google’s Ideological Echo Chamber,”, is...
-

Existentialism: Crash Course Philosophy #16
Video In this video, Crash Course covers the philosophical idea of essentialism and its response – existentialism. The video then discusses...
-

Existentialism Is a Humanism
The description for this book is as follows: "It was to correct common misconceptions about his thought that Jean-Paul Sartre,...
-

Existentialist Praxis Beyond Marxist Idealism, or: How Can Sartre Help Us Today?
Article In this blog post in Columbia Law's Critique, Ringleb argues that Sartre's notion of seriality, or the formation of in-groups based...
-

Exploding the Phone
Book This book provides an in-depth historical perspective and study of phone phreaking and hackers of the telecommunication industry known as phone...
-

Facebook And Our Phones May Be Wreaking Havoc On Our Morality - Vox
Article Digital distractions such as social media and smartphones wreak havoc on our attention spans. Could they also be making us...
-

Facebook, Google and Netflix pay a higher median salary than Exxon, Goldman Sachs or Verizon
Article In this article, the author discusses how employees at several major tech corporations make more than their counterparts in major business/banking corporations....
-
Facebook Knew I Was Gay Before My Family Did
Article This article tells the story of a closeted gay Facebook user who received targeted ads offering assistance with coming out. The...
-

Facebook Knows Instagram Is Toxic for Teen Girls, Company Documents Show
Article In this article, take a look at Facebook's own in-depth research which shows a significant teen mental-health issue. Thus far, Facebook has...
-

Facebook scientists say they can now tell where deepfakes have come from
Article This article describes deepfake detection software created by Facebook and Michigan State. The software is able to determine not only...
-

Facebook Tried to Make Its Platform a Healthier Place. It Got Angrier Instead.
Article In this article, the authors discuss Facebook's internal memos which show how a big 2018 change rewarded outrage and how CEO...
-

Face-Off Lecture Slides
Lecture / slides Slides for Lecture 21 of Ethical and Professional Issues in Notre Dame's Computer Science and Engineering department. The learning goals...
-

FACT CHECK: Do Robots Or Trade Threaten American Workers More?
Article This article fact checks claims made by Elizabeth Warren and Andrew Yang in a 2019 Democratic presidential debate regarding if...
-

Feds defend voluntary robot car regulations
Article This article describes the arguments for and against robot car regulations. While safety advocates argue for strict autonomous vehicle regulations, the...
-

Florida State Student Faces Felony Charges for Redirecting School's Wifi Users to Infamous Shock Site
Article This article tells the story of a Florida State student who faced felony charges after hacking the school’s wifi network...
-

Flow: The Psychology of Optimal Experience
The description for this book is as follows: "Legendary psychologist Mihaly Csikszentmihalyi's famous investigations of 'optimal experience' have revealed that...
-

Forced to Love the Grind
Article In this article, Miya Tokumitsu argues that the modern workplace pressures workers to "love to grind," a trend which is both counterproductive...
-

Forging Pathways to Purposeful Work: The Role of Higher Education
Report This report conducted jointly by Bates College and the Gallup organization highlights the importance of meaning and purpose for today's...
-

For Young Female Coders, Internship Interviews Can Be Toxic
Article In this article, it discusses a survey conducted by Girls Who Code where teen female engineers report that even their very...
-

Freedom Downtime
Video This video is the documentary from 2001 that is sympathetic to convicted computer hacker, Kevin Mitnick. It is produced by 2600...
-

From Anon to Alt-Right: The Dangerous Tricksters of 4chan
Article In this article, Joanne McNeil outlines how 4Chan's activist arm "Anon" moved evolved from genuine, albeit avant-garde, activism to a breeding...
-
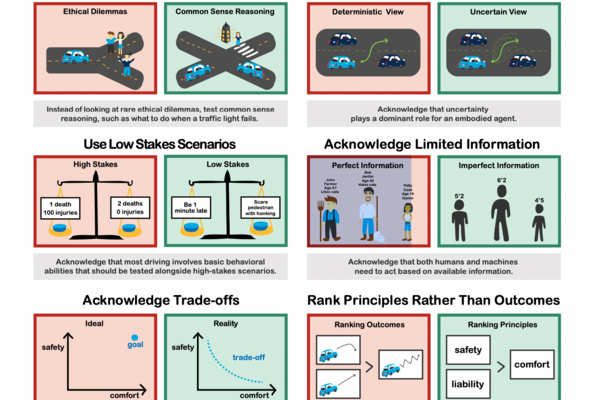
From driverless dilemmas to more practical commonsense tests for automated vehicles
Academic Paper This academic paper has the following abstract: "For the first time in history, automated vehicles (AVs) are being deployed in...
-

From Internet Farming to Weapons of the Geek
Article This article details the history of political hacking by Gabriella Coleman in which she provides an introduction and inventory of the...
-

From Memes to Infowars: How 75 Fascist Activists Were “Red-Pilled”
Article This article describes the "red-pilling" phenomenon--how people with mainstream beliefs are converted to far-right fascist ways of thinking. Specifically, this article...
-

Fueling the Hong Kong Protests: A World of Pop-Culture Memes
Article This article describes the pop culture memes employed by anti-government protestors in Hong Kong in 2019. The memes come from...
-

Future of Travel Lecture Slides
Lecture / slides Slides for Lecture 19 of Ethical and Professional Issues in Notre Dame's Computer Science and Engineering department. In this lecture, the...
-

GamerGate's Archvillain Is Really A Trolling Sketch Comedian
Article This article tells the story of Jan Rankowski, an Internet satiritst and comedian. Rankowski experienced harassment after he posted a video satirizing "GamerGaters"...
-

Give Up On Work-Life Balance
Article In this article, Olga Khazan argues that the best way to stay sane while managing work and life is to...
-
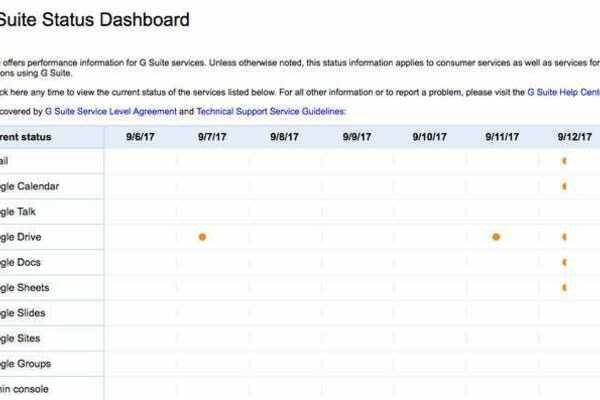
Gmail and other popular Google services experienced a partial service outage at a very bad time
Article In this article, Oreskovic reports on some of Google's most popular services, including Gmail and Google Calendar, that experienced technical...
-

GNU General Public License, v.2
Digital Artifact This digital artifact is a well known legal hack also known as a "copyleft" (a play on copyrights). The GNU Public License,...
-

God's Grandeur
Poem In this poem, Hopkins proclaims God's presence in the natural world, and bemoans humankind's severed connection to it. He laments...
-

Good Work
Book The description for this book is as follows: "What does it mean to carry out "good work"? What strategies allow...
-

Google Employee Alleges Discrimination Against Pregnant Women in Viral Memo
Article In this article, the authors discuss a memo written by a Google employee who was discriminated against for being pregnant,...
-

Google Employee Writes Memo About ‘The Burden of Being Black at Google’
Article In this article, a memo from a former Google employee is discussed. In the memo, the ex-employee criticized the internet...
-

Google Plus Finally Gives Up on Its Ineffective, Dangerous Real-Name Policy
Article This article celebrates Google Plus's riddance of a policy that required users to use their real names with their Google Plus...
-
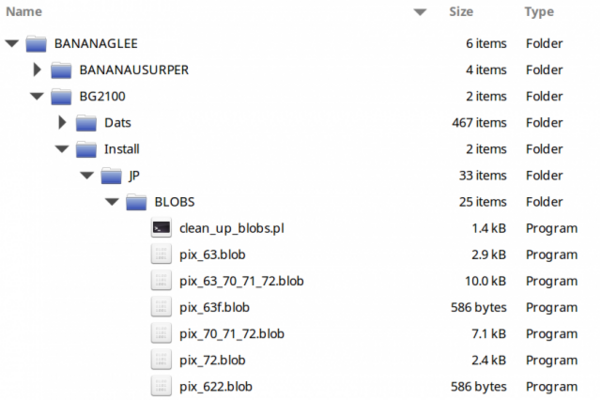
Group claims to hack NSA-tied hackers, posts exploits as proof
Article This article tells the story of a hacking group called the Shadow Brokers that claimed to have hacked the NSA's hacking...
-

Group Project 00: Your Upcoming Career in Tech
Group Project In this group project, students in the Ethical and Professional Issues course in Notre Dame's Computer Science and Engineering department...
-
Group Project 01: The Social Media Situation
Group Project In this group project, students in the Ethical and Professional Issues course in Notre Dame's Computer Science and Engineering department are...
-

Group Project 02: A Letter to the Editor from Citizens Concerned About AI
Group Project In this group project, students in the Ethical and Professional Issues course in Notre Dame's Computer Science and Engineering department are...
-

Group Project 03: A Visual Guide to Security and Privacy
Group Project In this group project, students in the Ethical and Professional Issues course in Notre Dame's Computer Science and Engineering department are...
-

Guardian of the GPL: Online advertising is becoming “a perfect despotism”
Article In this article, the author provides an overview of Eben Moglen (Guardian of the GPL)' s thoughts on why online...
-

H-1B: Foreign citizens make up nearly three-quarters of Silicon Valley tech workforce, report says
Article In this article, Ethan Baron reports on the reality that a majority of Silicon Valley and Seattle-area tech workers are...
-

H2K2: The Conscience of a Hacker
Video This video is of the hacker who goes by the handle The Mentor reading his famous essay from 1986, titled "The...
-

Hacker Activism of the Guacamaya
Video This video is by the international environmental hacking group known as the Guacamaya. The group has published anonymous reports and leaked sensitive files...
-

Hacker Crackdown: Law and Disorder on the Electronic Frontier
Book Chapter This book details the spirit of the times with the criminalization (and eventual crackdown) of the so-called "hacker underground." This particular...
-

Hacker Documentary: Unauthorized Access by Annaliza Savage [1994]
Video This video has the following YouTube description: This is a nostalgic hacker documentary about the early to mid 90s computer...
-

Hackers and Painters
Article In this essay, Dr. Graham addresses creativity, time, and success in technology.
-

Hackers: Heroes of the Computer Revolution
Book Steven Levy's book is is a classic text on the history of computing. It is used throughout the course to highlight the hacker...
-
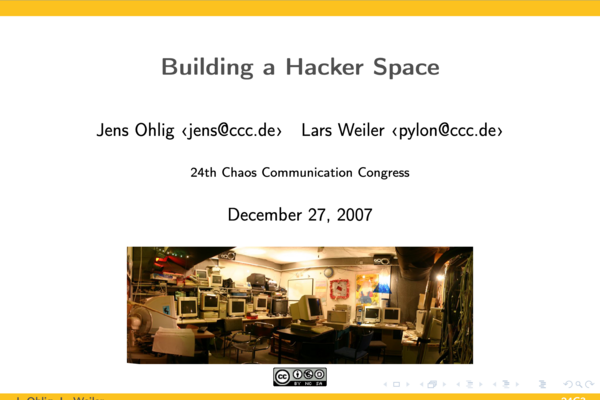
Hacker Space Design Patterns
Lecture / slides This document is a set of slides from Jens Ohlig and Lars Weiler for the 24th Chaos Communication Congress about Building a...
-

Hackers Testimony at the United States Senate
Video This video depicts the testimony of the hacker group, L0pht Heavy Industries, in front of the United States Senate in 1998. The...
-

Hackers - Wizards of the Electronic Age
Video This video is a short documentary about the hacker underground and the foundations of the hacker ethic. From the video description,...
-
Hacking at the Crossroad: U.S. Military Funding of Hackerspaces
Article This article is an influential piece written by the inventor Mitch Altman about the influence of defense funding in technological development. It...
-
Hacking Security
Article In this article, the authors argue that today's security issues are not information security threats, but rather "abuse." Abuse is...
-
Have Autonomous Vehicles Hit A Roadblock?
Article This article argues that despite promises to have fully autonomous vehicles hit the roads around 2021-2022, the reality is that they...
-

Have Better Days With Marcus Aurelius' Daily Routine | Ryan Holiday on Practicing Stoicism
Video In this video, Ryan Holiday explores some of Marcus Aurelius' tips for living a better life. He explains how Aurelius...
-
Hegel & Labour
Other In this talk by Paul Ashton, he lays out Hegel's view of labor and it application to today. Hegel, according...
-

Here Comes The Robot Revolution Lecture Slides
Lecture / slides Slides for Lecture 18 of Ethical and Professional Issues in Notre Dame's Computer Science and Engineering department. In this lecture, the...
-

Here's How Google Makes Sure It (Almost) Never Goes Down
Article In this article, take a look at a new book that peers into the system that keeps Google up and...
-

Hiring is Broken And Yours Is Too
Article In this article, Prabhakar discusses various interview practices and why "everyone’s hiring practices are broken".
-
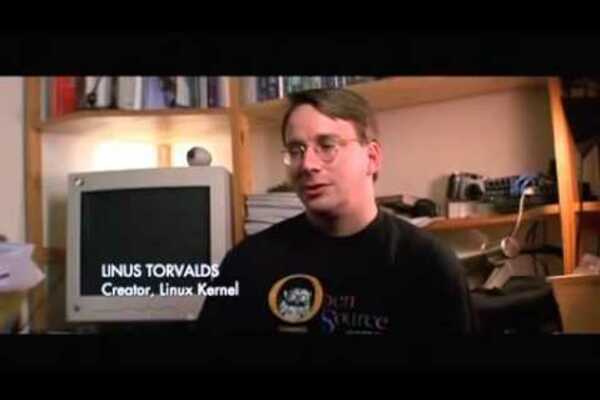
History of Gnu, Linux, Free and Open Software
Video This video depicts the history of the open source and free software movements including the history and technological development of Gnu and...
-

HoHoCon 1992 Miscellany
Article This text file describes how "Project Green Cheese" came up at HoHoCon 1992. For context, this text file should be considered...
-

How Artificial Intelligence and Robots Will Radically Transform the Economy
Article This article discusses how automating away jobs isn’t always a bad thing. The article begins with the example of automated...
-

How bosses are (literally) like dictators
In this article, Elizabeth Anderson argues that businesses are a form of government, and that workplaces are predominantly spaces of...
-

How China uses facial recognition to control human behavior
Article This article describes China’s extreme usage of facial recognition surveillance. While in the US facial recognition surveillance is used to...
-

How Companies Learn Your Secrets
Article In this article, the author tells the story of how Target learned to identify when women are pregnant to target...
-

How Computer Science at CMU Is Attracting and Retaining Women
Article In this article, it discusses how CMU has attracted a higher rate of women in its computer science program than...
-

How Congress Censored the Internet
Article This article discusses the Allow States and Victims to Fight Online Sex Trafficking Act (FOSTA) that undermines Section 230 to make...
-

How Dangerous is Cyberbullying?
Article In this article, George Beall describes the current state of cyberbullying. The article includes who is being cyberbullied, motivations for cyberbullying,...
-
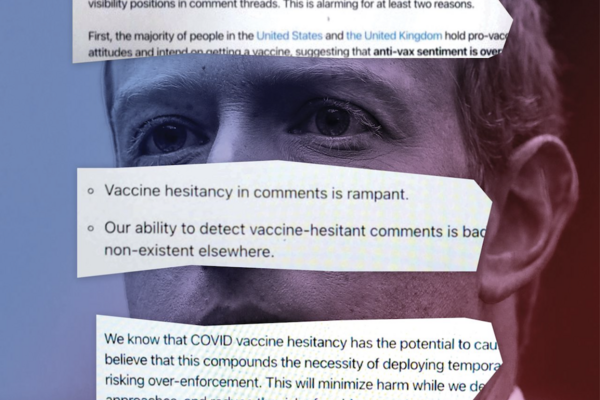
How Facebook Hobbled Mark Zuckerberg’s Bid to Get America Vaccinated
Article In this article from the Wall Street Journal's Facebook Files, the authors describe how despite Facebook's best efforts to promote true...
-

How Facial Recognition Is Fighting Child Sex Trafficking
Article This article discusses how facial recognition technology is being used to fight child sex trafficking. The Spotlight tool matches faces...
-

How Facial Recognition Technology Is Helping Identify the U.S. Capitol Attackers
Article This article describes how facial recognition technology was used to identify people who participated in the January 6, 2021 attacks...
-

How Far Did Plato And Xenophon Support The Division Of Labour?
Article In this article, Sena Özyapı discusses the ancient roots of Adam Smith's idea of division of labor. She focuses on two...
-

How goatse.cx went from shock site to webmail service
Article This article tells the story of the website goatse.cx. Originally a shock site with an awful image, the domain was purchased...
-

How Hackers Broke Into Real News Sites to Plant Fake Stories
Article This article describes how a hacking group targeted Eastern European countries with disinformation campaigns. Their strategy was to hack the content...
-

How Jair Bolsonaro used ‘fake news’ to win power
Article This article tells the story of how Jair Bolsonaro was elected president of Brazil in 2018. His campaign strategy involved the...
-

How Life Became an Endless, Terrible Competition
Article In this article, talks about the costs of the meritocracy. Meritocracy prizes achievement above all else, making everyone—even the rich—miserable. The...
-

How Millennials Became The Burnout Generation
Article In this article, Peterson explains how the stereotypes commonly associated with millennials - lazy, entitled, spoiled - can mostly be...
-

How Much Is Enough?
The description for this book is as follows: "What constitutes the good life? What is the true value of money?...
-

How Much Surveillance Can Democracy Withstand?
Article This article discusses how limits must be put on surveillance in order to maintain a healthy democracy. The author poses...
-

How Noncompete Clauses Keep Workers Locked In
Article In this article, the author discusses restrictions that were once limited to executives which are now spreading across the labor landscape....
-

How not to bomb your offer negotiation
Article In this article, Qureshi discusses what to do after you've landed your dream job. He takes a deep-dive into the negotiating process...
-

How Russian Trolls Used Meme Warfare to Divide America
Article This article describes how the Internet Research Agency (IRA), a Russian propaganda wing, infiltrated American social media users’ feeds with...
-

How the Apple-1 Works
Video This video provides a technical overview of the Apple-1 Computer. The technical aspects of the computer are described and shown as...
-

How the Bobos Broke America
Article In this article, the author discusses how the creative class was supposed to foster progressive values and economic growth. The...
-

How to Care Less About Work
Article In this article, Charlie Warzel and Anne Helen Peterson argue that American working culture is unsustainable. Warzel and Peterson ask: when...
-

How to Deal With Deceptive Colleagues at Work
Article In this article, the author describes ways in which employees deceive their coworkers and how deceptive behaviors lead to a...
-

How to Fight Fake News on Vaccines
Video This video explains how misinformation spread about the HPV vaccine and how one woman with cervical cancer fought to reverse that...
-

How to find a meaningful job, or find purpose in the job you already have
Video From the video description: "Broaching the question 'What is my purpose?' is daunting – it's a grandiose idea, but research...
-

How to Find Fulfilling Work
Video This short video from "The School of Life" offers a framework and practical tips for finding work that is fulfilling,...
-

How to Have Moral Courage and Moral Imagination?
Video Every time we make a decision, we change the world just a little bit. This is why moral imagination plays...
-

How to Improve Capitalism
Video In this video, The School of Life provides four suggestions for reforming capitalism. First, there are many types of capitalism,...
-
How to keep your team motivated
Video In this video, the Kellogg School lays out ways business leaders can counteract the Social Loafing effect, the tendency for...
-
How to make AI less racist
Article This article discusses how negative biases, for example racial biases, can be baked into artificial intelligence algorithms through the use...
-

How to Recognize Burnout Before You're Burned Out
Article This article explains what burnout is and enumerates common work stressors, signs of burnout to watch for, and ways to combat burnout...
-

How to Work Hard
Article In this article, Graham address working hard and lessons he's learned.
-

How WhatsApp Destroyed a Village
Article This article discusses how false information about child abductions circulating WhatsApp in India caused at least 29 deaths from people attacking...
-

HyperNormalisation
Video In this video, Adam Curtis, a cult documentary maker, explores the falsity of modern life in his own inimitable style. Though he’s...
-

IBM Punch Card
Digital Artifact This article describes the history of the IBM Punch Card technology such as its technical development and its cultural impact. This...
-

‘I made Steve Bannon’s psychological warfare tool’: meet the data war whistleblower
Article In this article, Christopher Wylie, a young man who was the brains behind Cambridge Analytica, comes forward to share his...
-

Immigrants Help Solve the Looming STEM Worker Shortage
Article In this article, the author promotes a looser immigration policy for foreign skilled workers. The author argues that there are not...
-

Incels Categorize Women by Personal Style and Attractiveness
Article This article describes the “Intel” Internet subculture. “Incels” are “involuntarily celibate” men—men who not only struggle to find sexual partners,...
-

In Silicon Valley, Working 9 to 5 Is For Losers
Article In this article, Dan Lyons describes the "Hustle Culture" phenomenon in Silicon Valley, where workers idolize overworking. Lyons outlines some...
-

Interns’ Job Prospects Constrained by Noncompete Agreements
Article In this article, Harriet Torry discusses legal pacts that can limit résumé content and employment options, including those for interns.
-

In This Economy, Quitters Are Winning
Article In this article, the authors discuss an increase in job-hopping which may give way to wage growth and productivity in...
-

Introducing the LAN Turtle
Video This video is an introduction to the LAN Turtle by Hak5 an infosec company founded in 2005. From the video description, "The LAN...
-

Inventing Copyleft
Article This book chapter is from Christopher Kelty's book called "Two Bits: The Cultural Significance of Free Software" that details the history of Free...
-

Is Facebook Making Us Lonely
Article In this article, Stephen Marche talks about how even though social media has made society more densely networked than ever, it may be making...
-

Islamic State’s TikTok Posts Include Beheading Videos
Article This article discusses how the Islamic state posted videos of executions and tortures to Tik tok. These videos are a...
-

Is life meaningless? And other absurd questions
Video In this video, TED-Ed discusses Albert Camus. It offers some biographical background before exploring his philosophy. The video separates his...
-
Is Net Neutrality Good or Bad for Innovation?
Article This article outlines the arguments surrounding net neutrality and its effect on the economy. There is no clear answer--economists have modeled...
-

I Spent 24 Hours in the Metaverse. I Made Friends, Did Work and Panicked About the Future.
Article This article is a journalist's reflections on spending 24 hours using Meta's Oculus Quest 2 virtual-reality headset. She noted that Metaverse meetings are...
-

Is the H-1B Program a Cynical Attempt to Undercut American Workers?
Article In this article, Derek Thompson looks at the pros and cons of the H1-B Visa program. While he concedes that...
-

“It Gets Better”: Internet memes and the construction of collective identity
Academic Paper This academic paper has the following abstract: In September 2010, a video titled “It Gets Better” was uploaded to YouTube,...
-

It's hard to be a moral person. Technology is making it harder.
Article Digital distractions such as social media and smartphones wreak havoc on our attention spans. Could they also be making us...
-
I've spent 2 decades studying how work affects our health and well-being, and one solution is clear: Your job has to serve a purpose beyond a paycheck
Article In this article, which is an excerpt from Rath's book "Life's Great Question: Discover How You Contribute To The World,"...
-

I Was a Stranger Lecture Slides
Lecture / slides Through these lecture slides for Notre Dame Computer Science and Engineering's Ethical and Professional Issues course, the following learning goals are...
-

Join Wall Street. Save the World.
Article In this article, Matthews writes about Jason Trigg, a bright young man who decided to become a hedge fund manager...
-
Julian Assange: The 2011 60 Minutes Interview
Article From the video description: Steve Kroft interviews the controversial founder of WikiLeaks. For more, click here: https://www.cbsnews.com/news/julian-assange-the-2011-60-minutes-interview/
-

Just Because You Always Hear It, Doesn’t Mean It’s True: Gender Difference Explanations For Disparities in Tech Are Not Supported by Science
Article In this article, NCWIT explains why gender differences are not supported by science, and how most disparities between men and women...
-

Kant and Categorical Imperatives: Crash Course Philosophy
Video In this video, get a crash course on Kant and Categorical Imperatives. Categorical Imperatives are unconditional moral obligations which are binding in all...
-

Karl Marx on Alienation
Video In this video, BBC Radio explains Marx's views on alienation. According to Marx, authentic work is what makes us human....
-

Keystroke tracking, screenshots, and facial recognition: The boss may be watching long after the pandemic ends
Article This article describes how companies track their employees through video feed data/facial recognition, keystroke tracking, and screenshots. This type of...
-
Kindness is Underrated
Article In this article, the author responds to Linus Tovalds’s tendency towards blunt, crass criticism with an argument for kindness. The...
-

Leaking Like A Sieve Lecture Slides
Lecture / slides Slides for Lecture 25 of Ethical and Professional Issues in Notre Dame's Computer Science and Engineering department. The learning goals for...
-

Lean In: Study of Women in Corporate America
Report In this report, LeanIn.Org and McKinsey & Company studied over 750 companies over the course of the last 6 years (2015-2021) to...
-

Legal Shield for Websites Rattles Under Onslaught of Hate Speech
Article This article discusses Section 230 of the Communications Decency Act, which protects Internet companies from liability for content created by their...
-

Leisure: The Basis of Culture
Philosophical Text From the book description: "One of the most important philosophy titles published in the twentieth century, Josef Pieper's Leisure, the...
-
Lets talk about the H-1B Visa
Article In this article, the author describes the drawbacks of the current H-1B Visa program and proposes reforms so the program...
-

Linus Torvalds defends his right to shame Linux kernel developers
Article In this article, we see the interactions between the crass Linux creator Linus Torvalds and software developer Sarah Sharp. Sharp...
-

Linus Torvalds: 'I'll never be cuddly but I can be more polite'
Article In this article, Linus Torvalds admits that his interactions within the Linux developer community were rather strong while distancing himself...
-

Linus Torvalds on his insults: respect should be earned
Video In this video, Linus Torvalds (creator of Linux and Git), defends abrasive comments he makes towards other codes (e.g. "you...
-

Linux Operating System
Digital Artifact This article describes the digital artifact of the Linux Operating System which is a family of open-source Unix-like operating systems based on...
-

Loving Your Job Is a Capitalist Trap
Article In this article, Erin A. Cech claims that the pandemic forced Americans to reflect on their satisfaction with their work lives, prompting...
-
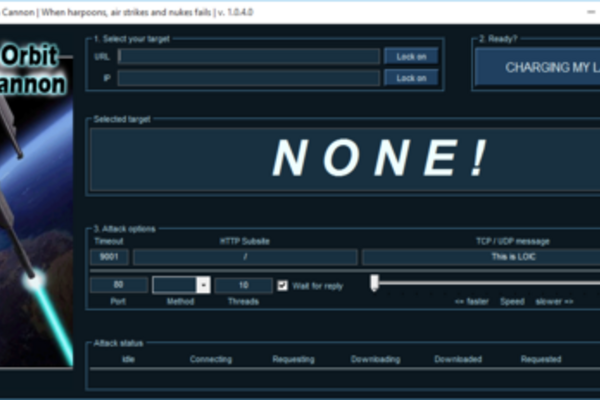
Low Orbit Ion Cannon
Digital Artifact This article describes the digital artifact Low Orbit Ion Cannon which was originally created by Praetox Technologies. The Low Orbit Ion Cannon...
-

Machines, Modifications of Nature, and Engineering Ethics
Article In this article, the author argues that while codes of conduct are important, they are not sufficient in solving the...
-

Major camera company can sort people by race, alert police when it spots Uighurs
Article This article describes a facial-recognition technology by the Chinese company Dahua that is tuned to spot Uighurs, a minority ethnic...
-

Making sense of work: finding meaning in work narratives
Article The abstract for this article is as follows: "This study examined how individuals make sense of their work narratives –...
-

Masters of Crowds: The Rise of Mass Social Engineering
Article This article provides a deep history of mass manipulation from the 1920s through the mid-1970s. This article is adapted from the...
-

Maybe We All Need a Little Less Balance
Article In this article, Brad Stulberg argues that balance is not something we should strive for. Stulberg argues that people are...
-

Meditations (Marcus Aurelius)
Philosophical Text In this classic work of stoic philosophy, Roman Emperor Marcus Aurelius writes notes to himself recording his thoughts on the good...
-

Memes Against Decadence
Article In this article, Ross Douthat explores how memes and other virtual "realities" can exist long enough to change the real...
-

Memes in a Digital World: Reconciling with a Conceptual Troublemaker
Academic Paper This academic paper has the following abstract: This paper re-examines the concept of “meme” in the context of digital culture....
-

Memetic Warfare Lecture Slides
Lecture / slides Slides for Lecture 15 of Ethical and Professional Issues in Notre Dame's Computer Science department. In this lecture, the following...
-

Metaethics: Crash Course Philosophy #32
Video In this video, Crash Course covers metaethics – which probes the foundation of morality. The video begins by distinguishing metaethics from...
-
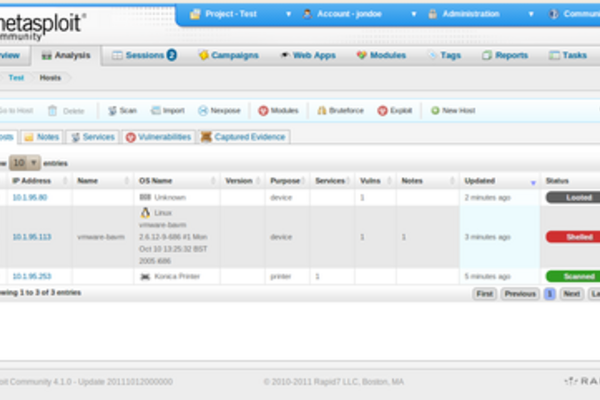
Metasploit Framework
Digital Artifact This article details the digital artifact the Metasploit Framework or the Metasploit Project. This artifact is a computer security project that...
-

Michael Sandel: 'The populist backlash has been a revolt against the tyranny of merit'
Article In this article, Coman explains the views on meritocracy of Michael Sandel, one of the leading critics of free-market orthodoxy today....
-

Midlife
Book The description for this book is as follows: "How can you reconcile yourself with the lives you will never lead,...
-

Mindset
Book The description for this book is as follows: "'It’s not always the people who start out the smartest who end...
-

MIT Report Examines How to Make Technology Work for Society
Article This article describes the findings from MIT’s Task Force on Work of the Future. The report finds that while the...
-

Modern Porn Education Is Totally Unprepared for Modern Porn
Article This article highlights the need for teenagers to have porn literacy. The proliferation of extreme pornography can numb viewers of...
-

More and Faster
Lecture / slides Lecture slides for Lecture 08 of Ethical and Professional Issues in Notre Dame's Computer Science & Engineering department. These lecture slides cover...
-

Most computer science majors in the U.S. are men. Not so at Harvey Mudd
Article In this article, it takes a look at Harvey Mudd where more than half of computer science graduates are women.
-

My Job, My Self: Work and the Creation of the Modern Individual
Book From the book description: "In My Job My Self, Gini plumbs a wide range of statistics, interviews with workers, surveys from employers...
-

Naive Meritocracy and the Meanings of Myth
Article In this article, Reagle proposes that so-called meritocracies reproduce extant members and favor incidental attributes; they are biased, susceptible to...
-

Narrative technologies meets virtue ethics in alternate reality: investigating the possibility of a narrative virtue ethics of technology, using the example of pokémon go
Academic Paper This academic paper has the following abstract: Virtue ethics offers a promising starting point for thinking about ethics of technology....
-

Nerdy Strutting: How to Put Women Off the Tech Industry
Article In this article, Judy Robertson discusses nerd-strutting, or "a style of interaction where people show off their knowledge by asking questions...
-
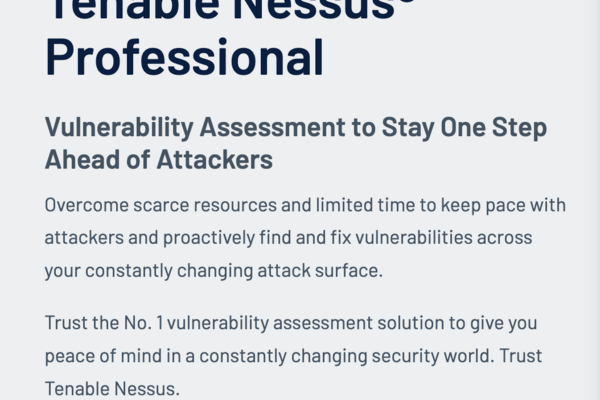
Nessus Proprietary Security Scanner.
Digital Artifact This technology is a digital artifact by Tenable which is the Nessus Properitary Security Scanner. This technology is properitary software from...
-

Network Mapper (nmap)
Digital Artifact This article presents the Network Mapper (nmap) tool created by Gordon Lyon who is also known by the psuedonym Fyodor Vaskovich. This tool...
-

New Melleray Abbey: One Thing
Video In this documentary video, the life of monks at the New Melleray Abbey is explored. At this monastery outside of...
-

New Seeds of Contemplation
Book The discription for this book is as follows: "New Seeds of Contemplation is one of Thomas Merton’s most widely read and...
-
.nfo File
Digital Artifact This article describes a digital artifact known as the .nfo file extension which is a shortening of info or information. This...
-

Noncomplete Clause Causes Pop Up in Array of Jobs
Article .In this article, the author shares their opinion on how supporters of the pending legislation argue that the proliferation of noncompetes is...
-

Note to employees from CEO Sundar Pichai
Article In this article, Google CEO Sundar Pichai responds to Damore's memo.
-

Not Everyone in Tech Cheers Visa Program for Foreign Workers
Article In this article, the authors highlight stories of American tech workers who lost their jobs to foreign H1-B Visa holders....
-

Nvidia faked part of a press conference with a CGI CEO
Article This article describes how Nvidia used a CGI/deepfake version of their CEO to give a portion of a keynote speech at a...
-

One Month, 500,000 Face Scans: How China Is Using A.I. to Profile a Minority
Article This article describes how China is using facial recognition technology to track the Uighurs, a minority ethnic group in China....
-

OnlyFans Is Not a Safe Platform for ‘Sex Work.’ It’s a Pimp.
Article In this article, the author argues that “sex work” is neither sex nor work, and that calling it that is...
-
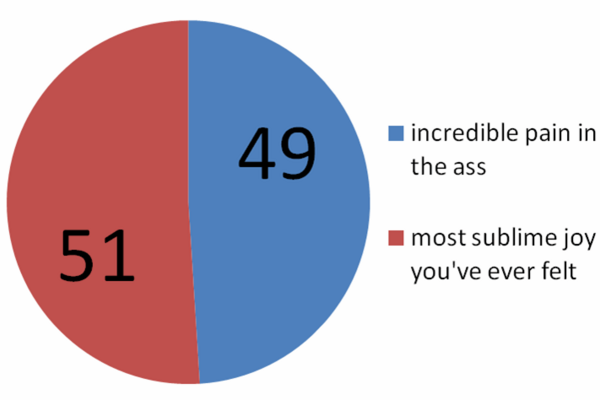
On Parenthood
Article In this article, prominent software developer Jeff Atwood describes his love of fatherhood and how parenthood has changed him for...
-

On the Orders of Work (Excerpts from Aristotle's "Politics")
Philosophical Text In these excerpts from Aristotle's Politics, he explores the proper relationship between work, education, and government in a well-ordered society.
-

On the Precipice? Lecture Slides
Lecture / slides Lecture slides for the introductory lecture of Ethical and Professional Issues (in Computer Science). In this lecture, the following learning...
-
On the Virtual Frontier of the Imagination
Book In this book chapter, Walter Scheirer discusses a very early instance of faking the news in which a group of...
-
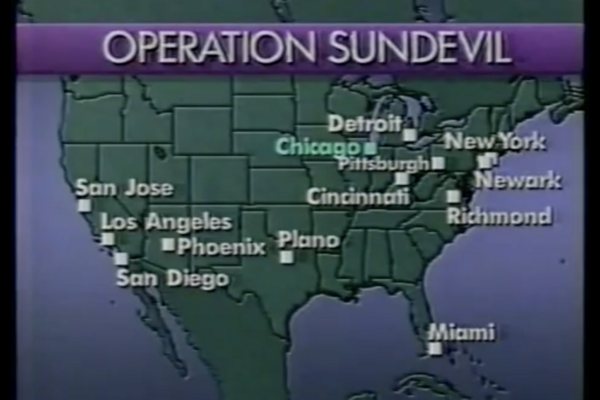
Operation Sundevil
Video The video provides a brief overview of Operation Sundevil from the 1990s. The operation was apart of a large hacker crackdown...
-

Optimal Work
Other Optimal Work is a paid service that aims to develop in its customers the ability to work optimally, free from anxiety, distraction,...
-

Our Real Work
Poem It may be that when we no longer know what to do we have come to our real work, and...
-

Owning Ethics: Corporate Logics, Silicon Valley, and the Institutionalization of Ethics
Article In this article, the authors study the attempts to institutionalize ethics within Silicon Valley tech companies. Through interviewing those responsible for thinking...
-

Paul Graham has accidentally explained everything wrong with Silicon Valley’s world view
Article In this article, the author counters some of the points that Paul Graham made in his article on Economic Inequality. She...
-

PERUSALL Tutorial: Introduction to the platform
From the video description: Here is an overview tutorial of what and how you can transform individual reading task to...
-

Philosophy & Ethics of Technology | Is Technology Good, Bad or Neutral?
Video In this video, the ideas and arguments from the philosophy paper "Is Technology Value Neutral?" by Boaz Miller are covered....
-

Philosophy: Thomas Aquinas
Video In this video, The School of Life discusses the philosophy of Thomas Aquinas, specifically his attempts to reconcile faith and...
-

Phone Phreaking: A Call From Joybubbles
Video This video depicts a phone phreaking call made by the hacker Joybubbles aka Josef Engressia, Jr. This original sound byte comes...
-

Photoshop Fantasies
Book In this piece, Walter Scheirer discusses the history of image manipulation. Although image manipulation is generally considered to be dishonest, Scheirer...
-

Phrack Magazine
Digital Artifact This digital artifact is an issue of Phrack Magazine which was and still is a popular zine for the underground hacking...
-

Phrack Magazine - Issue 31
Article This article is an introduction to Issue 31 of the popular underground hacking publication of Phrack Magazine. This particular article details...
-

Physiognomy's New Clothes
Article In this article, the authors discuss the history of physiognomy, or "scientific racism," and how some machine learning scientists today...
-
Pillar Investigates: USCCB gen sec Burrill resigns after sexual misconduct allegations
Article This article describes how Monsignor Jeffrey Burrill, Catholic priest and former general secretary of the U.S. bishops’ conference, was accused of sexual...
-

Pitfalls in Machine Learning Research: Reexamining the Development Cycle
Academic Paper This academic paper has the following abstract: Applied machine learning research has the potential to fuel further advances in data science,...
-

Plato and Aristotle: Crash Course History of Science #3
Video In this video, Crash Course introduces the basics of Plato's and Aristotle's lives and philosophies.
-

Plato's Best (And Worst) Ideas
Video In this video, TED-Ed lays out in broad terms the main ideas of Plato, and some of the consequences (good...
-

Political tension at Google is only getting worse
Article In this article, another former engineer has alleged that the company fired him over his political beliefs.
-

Posting less, posting more, and tired of it all: How the pandemic has changed social media
Article In this article, it examines how after one year, Covid-19 has altered how people use social media.
-

Privacy Fundamentalism
Article In this article, the author argues that there are alarmist privacy arguments out there and explains why one by Farhad...
-

Process (Excerpt from "Games and Why They Matter: A Conversation with Thi Nguyen")
Video In this video, narrator Thi Nguyen describes the value in work as process rather than product. He connects this to...
-

Programmers: Stop Calling Yourselves Engineers
Article In this article, the author argues that programmers should stop calling themselves engineers. The author argues that "engineering" implies a...
-

Programming, Power, and Responsibility
Article In this article the author forms a metaphor of code as a social contract and reflects on the power given to...
-

Protesters are weaponising memes to fight police surveillance
Article This article describes how amidst the Black Lives Matter/anti-police brutality protests of spring 2020, memes were used as a tool...
-

Punching the Clock (from the book Bullshit Jobs)
Article In this excerpt published by Harper's Magazine from his work Bullshit Jobs, Graeber explores why it is that meaningless work makes us so...
-

Push for Gender Equality in Tech? Some Men Say It’s Gone Too Far
Article In this article, it discusses how some men have recently spoken out about their feelings on gender equality in tech.
-

Qanon Deploys 'Information Warfare' to Influence the 2020 Election
Article This article describes how the Qanon conspiracy theories infliltrate social media. The article argues that the spread of Qanon content signals a...
-

Ransomware attacks are getting more complex and even harder to prevent
Article This article discusses the threat of ransomware attacks. Ransomware attackers are launching attacks faster than vendors can patch the vulnerabilities, and...
-

Reading Quiz 01
Reading Quiz This reading quiz was used in the Ethical and Professional Issues course in the Computer Science and Engineering department at Notre...
-

Reading Quiz 02
Reading Quiz This reading quiz was used in the Ethical and Professional Issues course in the Computer Science and Engineering department at Notre...
-

Reading Quiz 03
Reading Quiz The third reading quiz for the Ethical and Professional Issues course in Notre Dame's Computer Science and Engineering department. The quiz...
-

Reading Quiz 04
Reading Quiz This reading quiz for the Ethical and Professional Issue course in Notre Dame's Computer Science and Engineering Department covers the following...
-

Reading Quiz 05
Reading Quiz This reading quiz covers the following readings: How bosses are (literally) like dictators (Anderson) The code I'm still ashamed of (Sourour)...
-

Reading Quiz 06
Reading Quiz This reading quiz from the Ethical and Professional Issues course in Notre Dame's Computer Science and Engineering department covers the following...
-

Reading Quiz 07
Reading Quiz This reading quiz from the Ethical and Professional Issues course in Notre Dame's Computer Science and Engineering department covers the following...
-

Reading Quiz 08
Reading Quiz This reading quiz was used in the Ethical and Professional Issues course in the Computer Science and Engineering department at Notre...
-

Reading Quiz 09
Reading Quiz This reading quiz for Ethical and Professional Issues in Notre Dame's Computer Science and Engineering Department covers the following readings: Why...
-

Reading Quiz 10
Reading Quiz This reading quiz was used in the Ethical and Professional Issues course in the Computer Science and Engineering department at Notre Dame....
-

Reading Quiz 11
Reading Quiz This reading quiz was used in the Ethical and Professional Issues course in the Computer Science and Engineering department at Notre...
-

Reading Quiz 12
Reading Quiz This reading quiz was used in the Ethical and Professional Issues course in the Computer Science and Engineering department at Notre...
-

Reading Quiz 13
Reading Quiz This reading quiz was used in the Ethical and Professional Issues course in the Computer Science and Engineering department at Notre...
-

Reconsidering Anonymity in the Age of Narcissism
Article In this article, Gabriella Coleman reflects on the importance of anonymity and how it is almost impossible on the Internet...
-

Red Box (Phreaking)
Article This article provides a technical description and history of the red box phone phreaking device. This device was created and utilized...
-

Reddit cracks down on abuse as CEO apologizes for trolling the trolls
Article This article describes how user trust in Reddit was compromised when the CEO used his admin access privilege to tamper with comments on r/the_donald....
-

Reddit Troll Ban Helped Cut Hateful Speech
Article This article discusses the results of a quasi-experiment on the effect of hate speech on Reddit after the banning of two subreddits full of...
-

Reflecting On One Very, Very Strange Year At Uber
Article In this article, Susan Fowler discusses her reasons for leaving Uber.
-

Reflecting on Susan Fowler’s Reflections
Article In this article, Aimee Lucido reflects on the article written by Susan Fowler, discussing her negative experience with Uber.
-

Reflections on Trusting Trust
Article This article is a written version of an Alan Turing Award Lecture from Ken Thomson in 1984. This article is a...
-

Remote OS detection via TCP/IP Stack FingerPrinting
Article This article is from issuse 54 of Phrack Magazine in 1998 written by Gordon Lyon aka Fydor, the creator of the...
-

Rene Carmille
Article This article details the life of Rene Carmille who is known to be one of the first hackers. This article gives a...
-

Representing Hacker Culture: Reading Phrack
Book Chapter This book chapter from Douglas Thomas' book Hacker Culture details an outsider's guide to reading the hacker zine Phrack. This chapter discusses...
-

“Repugnant” online discussions are not illegal thoughtcrime, court rules
Article This article describes a court ruling about disturbing sexual fantasies posted online. A US Federal Court of Appeals ruled that it is...
-

Researchers Create 'Master Faces' to Bypass Facial Recognition
Article This article describes how researchers generated nine "master key" fake faces that are able to impersonate almost half of the faces in...
-

Resistance to the current: the dialectics of hacking
Book Chapter This book chapter is titled "Internet Relay Chat: A Time Machine That Stood the Test of Time" and details the history...
-

Responses to Critiques on Machine Learning of Criminality Perceptions
Academic Paper In this academic paper and its response, the authors of a controversial paper that uses machine learning to determine criminality...
-

Rest
Book The description for this book is as follows: "Overwork is the new normal. Rest is something to do when the...
-
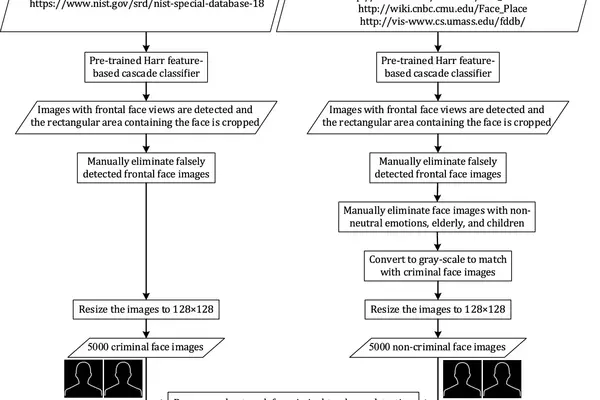
RETRACTED ARTICLE: Criminal tendency detection from facial images and the gender bias effect
Academic Paper This retracted academic paper seeks to predict criminality from facial images using deep learning. Other scientists criticize this work as having flawed methods.
-

Revisiting Meatspin, the NSFW site that shocked a generation
Article This article tells the story of the shocking website “meatspin” which depicted a penis spinning to the tune of Dead...
-

Revolutionary Aristotelianism: Ethics, Resistance and Utopia
The description for this book is as follows: "This book includes revisions of papers originally presented at the inaugural conference...
-

Salary Negotiation: Make More Money, Be More Valued
Article In this article, McKenzie discusses why negotiation matters, how to shift your mindset to embrace negotiation, and when/how a negotiation happens.
-

Scheirer on Fake Content
Video In this video, Walter Scheirer talks about his research and insight into fake content on the internet, today and throughout its...
-

Scheirer on Improving Tech
Video From the video description: Prof. Walter Scheirer (Computer Science, University of Notre Dame) thinks about the state of the tech...
-

Scheirer on Start-ups
Video In this video, Dr. Walter Scheirer discusses the benefits of starting your own start-up rather than working for an established company...
-
Scheirer on Tech Ethics
Video In this video, Dr. Sheirer gives an introduction to tech ethics.
-

Science Fiction Lecture Slides
Lecture / slides Slides for Lecture 22 of Ethical and Professional Issues in Notre Dame's Computer Science and Engineering department. The learning goals for...
-

Seeing Is Believing Lecture Slides
Lecture / slides Slides for lecture 20 of Ethical and Professional Issues in Notre Dame's Computer Science and Engineering department. In this lecture, the...
-

Self-driving car accidents: Robot drivers are ‘odd, and that’s why they get hit’
Article This article describes a surprising reason why self-driving vehicles get into accidents: they are too cautious. The article argues that because...
-

Self-driving cars still can’t mimic the most natural human behavior
Article In this article, the author argues that in order to have safer self-driving cars, the cars need to be able to mimic...
-

Self-Driving Cars Still Don't Know How to See
Article In this article, Meredith Broussard highlights the dangers of self-driving cars. Broussard expands upon the fact that cars don't see...
-

Senate passes controversial online sex trafficking bill
Article This article describes an online sex trafficking bill passed by the Senate in 2018. The bill, called the Allow States and Victims...
-

Sex and STEM: Stubborn Facts and Stubborn Ideologies
Article In this article, the authors discuss their thoughts on the "sex differences" in STEM.
-

Shop Class As Soulcraft: An Inquiry into the Value of Work
Book This bestselling book is described by IndieBound as "A philosopher/mechanic's wise (and sometimes funny) look at the challenges and pleasures of working...
-

Should I Always Listen to My Boss? Lecture Slides
Lecture / slides Slides for Lecture 10 of Ethical and Professional Issues in Notre Dame's Computer Science and Engineering Department. This lecture covers...
-

Should Work Be Passion, or Duty?
Article In this article, Firmin DeBrabander points out that, as factors like productivity and quality of life increase, other countries are working less...
-

Silicon Valley Isn't a Meritocracy. And It's Dangerous to Hero-Worship Entrepreneurs
Article In this article, it discusses meritocracy and entrepreneurialism reinforce a closed system of privilege. It also reveals the threadbare nature...
-

Silicon Valley's “Body Shop” Secret: Highly Educated Foreign Workers Treated Like Indentured Servants
Article In this article, NBC's Bay Area Investigative Unit and The Center for Investigative Reporting report on an organized system for supplying cheap...
-

Silicon Valley's Unchecked Arrogance
Article In this article, the author argues that the idea of Universal Basic Income comes from Silicon Valley’s arrogant view toward...
-

Smashing the Stack for Fun and Profit
Article This article is from issue 49 of Phrack Magazine written by Elias Levy who also goes by the handle Aleph One in...
-
Sniffer FAQ
Article This article is written by an early computer security company founded in 1994 and later was acquired by IBM in 2006....
-

Snuff: Murder and torture on the internet, and the people who watch it
Article This article discusses shocking and gruesome content online and the people who view it. The viewers of gruesome content online...
-
Social Engineering A Way of Life
Article This article is written by the hacker Malefactor [OC] in textfiles.com which provides a guide to hackers and phreaks on social...
-
So Much for Decentralized Internet
Article In this article, Georgia Tech professor Ian Bogost makes an urgent argument in The Atlantic that the commercialization and centralization of the internet puts...
-
Spacewar!
Digital Artifact This game is a digital artifact of a Javascript version of the popular Spacewar! video game that is one of the...
-
Stalking the Wily Hacker
Article This article tells the story of a hacker who penetrated Lawrence Berkeley National Laboratory in the 1980s. It provides an anecdotal perspective...
-

Status Anxiety
Book In this book, Alain de Botton explores the anxiety induced by fear of what others think of us. He explains...
-

Status Anxiety (Video)
Video In this video, The School of Life discusses status anxiety – the anxiety that arises when we get asked "what...
-

Stewardship of global collective behavior
Academic Paper Collective behavior provides a framework for understanding how the actions and properties of groups emerge from the way individuals generate...
-

Still the Trump social media ban
Article This article puts former president Donald Trump's social media ban in perspective by inviting readers to hypothetically consider their reactions if...
-

Storage Media
Article This article provides the technical developments of various data storage methods and mediums throughout history. These digital artifacts provide an understanding...
-

Study finds gender and skin-type bias in commercial artificial-intelligence systems
Article This article tells the story of how Joy Buolamwini, a Black researcher at the MIT Media Lab, discovered that facial...
-
Stuxnet Worm
Digital Artifact This article describes the history and technological development of the Stuxnet Worm. The Stuxnet Worm is a malicious computer worm that was...
-

Submit documents to WikiLeaks
Other This is the submission page to WikiLeaks: https://wikileaks.org/Press.html#submit_help_contact This page can be important for students to see as they learn about...
-

‘Success Addicts’ Choose Being Special Over Being Happy
Article In this article, Brooks compares the relentless pursuit of success to an addiction. He argues that work can be a...
-

Synthetic Media: How deepfakes could soon change our world
Article This article discusses deepfakes. Deepfakes are audio and video recordings that appear to be real, but actually use artificial intelligence...
-

Tech Giants, Once Seen as Saviors, Are Now Viewed as Threats
Article In this article, Streitfeld notes that at the start of this decade, the Arab Spring blossomed with the help of social media,...
-

Technical and Cultural Revolutions
Video This video is from OSCON 2014 and the keynote speaker Tim O'Reilly, the founder and CEO of O'Reilly Media. From the video...
-

Technology and the Virtues: A Philosophical Guide to a Future Worth Wanting
Book From the abstract of the book listed on the Oxford University Press Scholarship Online: "This book explores the implications of...
-

Ten Rules for Negotiating a Job Offer
Article In this article, the author provides 10 rules that can help job searchers negotiate with potential employers.
-

Terminating Service for 8Chan
Article This blog post from Cloudflare explains why two years after kicking The Daily Stormer off their network, they decided to stop...
-

The Age of AI Hacking Is Closer Than You Think
This article is adapted from A Hacker’s Mind: How the Powerful Bend Society’s Rules, and How to Bend Them Back, by Bruce...
-

The Alt-Right Are Savvy Internet Users. Stop Letting Them Surprise You
Article In this article, the author discusses how far-right influencers gain popularity on YouTube through gaming the "attention economy." The author...
-

The Art of Deception
Book This book is a digital artifact used in the course to represent the area of social engineering. The book details several...
-

The Art of Port Scanning
Article This article from issue 51 of Phrack Magazine is written by Gordon Lyon aka Fydor about the nmap network scanner. This article introduced...
-

The Best Action is the One in According with Universal Rules
Book In this book excerpt, James Rachels explains the Kantian view. This view states that people should always be treated as...
-

The Best Action is the One That Exercises the Mind's Faculties
Philosophical Text In this philosophical text, Aristotle discusses what constitutes an ethical action. He argues that an ethical action is one that...
-

The Best Action is the One with the Best Consequences
Book In this book excerpt, it examines three ethical models: utilitarian, Kantian, and Nicomachean. In studying the following sections, consider how...
-

The Bullet Journal Method
Book In this book, Carroll outlines his method for intentional living: the bullet journal. This is a mindfulness practice designed to increase...
-

The Burnout Society
Book In this book, philosopher Byung-Chul Han argues that the so-called advances of the 21st century were supposed to make our lives...
-

The Capital of Meritocracy is Silicon Valley, Not Wall Street
Article In this article, the author explains that meritocracy and entrepreneurialism reinforce a closed system of privilege. It also reveals the...
-

The Case For Doing Nothing
Article In this article, Olga Mecking introduces the Danish concept niksen--doing nothing. Mecking highlights the benefits of doing nothing from time to time--it...
-

The Case for Working With Your Hands
Article In this article, Crawford argues that work in the trades, while often considered lowly or a last resort, can actually...
-
The Children of Pornhub
Article This article exposes how easy it is for pornographic videos posted without the subject of the video’s consent and/or pornographic...
-

The code I'm still ashamed of
Article In this article, the author describes an experience he had as a young coder where his job required him to...
-

The compelling case for working a lot less
Article In this article, Amanda Ruggieri explores the compelling evidence against nonstop work, including that the work produced at the end...
-

The Conscience of a Hacker
Article This article was written by a computer hacker who went by the pseudonym The Mentor. The article sheds light on the...
-

The Convenience-Surveillance Tradeoff
Article In this article, Adrienne LaFrance discusses how Americans view the tradeoffs between privacy and surveillance based on a recent. Pew study....
-

The “Criminality from Face” Illusion
Academic Paper This academic paper has the following abstract: The automatic analysis of face images can generate predictions about a person’s gender,...
-

The Cult of Overwork
Article In this article, James Surowiecki argues that overwork is increasingly characteristic of high-paid workers. However, overwork worsens productivity and quality. The effects...
-

The Culture Wars Have Come to Silicon Valley 560
Article In this article, the author discusses the culture wars that have consumed politics in the United States and have now...
-

The Dangers of Having Too Little to Do
Video In this video, the School of Life argues that, while we think we'll be happy once the work is done,...
-
The Dehumanizing Myth of the Meritocracy
Article In this article, Ehmke looks at what happens when the meritocracy and open source software collide. She hopes to answer the...
-

The Division of Labor
Video In this video, Dr. van Heerikhuizen explains the impact of the division of labor, drawing on the first chapter of Adam...
-

The Driverless-Car Pile-Up
Article In this article, venture capitalist Michael Gibson describes his take on which autonomous vehicle companies to invest in. Gibson argues...
-

The Empathy Gap in Tech: Interview with a Software Engineer
Article In this article, Claire Lehmann interviews a talented engineer who is "not neurotypical" and discusses the lack of empathy in the...
-

The ethical foundations of economics in ancient Greece, focusing on Socrates and Xenophon
Other The abstract for this research article is as follows: Purpose Economics had a strong linkage to ethics up to the...
-

The existentialist’s reluctant guide to life
Article In this article, Ephrat Livni and Olivia Goldhill contend that even those who feel constant existential dread brings a sort of freedom....
-

The First Hacker
Video This video gives an overview of Rene Carmille's contribution as the first hacker. From the video description: "Based on the extraordinary...
-

The First Women in Tech Didn’t Leave—Men Pushed Them Out
Article In this article, Mims discusses the prevalence of sexism in the tech industry. In this article, hear female entrepreneurs and...
-

The Future of Not Working
Article In this article, Annie Lowrey investigates an experiment in universal basic income that is being run by the NGO GiveDirectly...
-

The Future Of The Culture Wars Is Here, And It's Gamergate
Article This article discusses how the GamerGate controversy fits in with the cultural context of the culture wars at large. After a...
-

The Future of Work in America
Report In this report, the McKinsey Institute analyzes the impact of automation on the US job market, looking both across time...
-

The Government's Fight to Make Encryption Illegal
Video This video is the third-part of a four part documentary by ReasonTV titled "Cypherpunks Write Code". From the video description: In 1977,...
-

The Hacker Conference: A Ritual Condensation and Celebration of a Lifeworld
Academic Paper This paper written by Gabriella Coleman, anthropologist and expert on all things computer hacking, provides a new scholarly perspective on hacker conferences....
-

The Hacker Crackdown (Complete Book)
Book The complete online version of the book The Hacker Crackdown. From Wikipedia: "The Hacker Crackdown: Law and Disorder on the...
-

The Hacker Hacked
Article This article discusses how the original hacker ethos was "gentrified" by yuppies. The original hacker ethos was wild with an outsider...
-

The Hackerspace Movement
Video This video is a Ted Talk given by Mitch Altman, the inventor and creator of the TV-B-Gone technology and famous hardware hacker....
-

The Hard Work of Being Lazy
Video In this video, The School of Life argues that sometimes it is difficult to be lazy enough. We ought to...
-

The Human Condition
Book The description for this book is as follows: "A work of striking originality, The Human Condition is in many respects more relevant...
-

The Improbability Party
Article This article discusses how data scientists try to predict the future why they will always have trouble when they try to...
-

The incredibly intricate badges of Def Con
Article This article details the creative badges created by hackers for their yearly hacking conference called DefCon. This article specifically details the...
-

The Intellectual Life
Book The description for this book is as follows: "Fr. Sertillanges's teachings are as timeless as any truths which describe the...
-

The Internet's public enema No. 1
Article This article discusses the shock content website Rotten.com. Rotten.com is a database of horrifying images that gets around 200,000 visitors...
-

The Irrelevance of Ethics
Book Chapter The abstract of this chapter is as follows:
-

The Light It Up Contest
Video This video is by the famous hacker George Hotz also known as Geohot. He is known for developing iOS jailbreaks, reverse engineering...
-

The Meaning of Life: A Very Short Introduction
Book The description of this book is as follows: "The phrase "the meaning of life" for many seems a quaint notion...
-

The Menace and Promise of Autonomous Vehicles
Article In this article, Jacob Silverman explores the issue of when autonomous vehicles make mistakes and cause accidents. Silverman highlights the...
-

The metaverse is here
Article In this article, Bruno Maçães discusses the Metaverse. He explains the technical specifications needed to support the Metaverse, imagines the user...
-

The Moral Complexities of Working With Julian Assange
Podcast From the podcast description: Many have considered Julian Assange, the founder of WikiLeaks, to be a hero of the free speech movement...
-

The Morality of Whistle-Blowing
Article From the article description: Computer scientists, like other professionals, may find a conflict between their loyalties and their obligation to...
-

The Most Good You Can Do
Book The description for this book is as follows: "Peter Singer’s books and ideas have been disturbing our complacency ever since...
-

The Myth of Sisyphus
Philosophical Text In The Myth of Sisyphus, Camus explores what he takes to be the absurdity of the human condition. He likens us...
-

The Need for Roots
Book The description for this book is as follows: "Hailed by Andre Gide as the patron saint of all outsiders, Simone...
-

The Need for Roots brought home the modern era's disconnection with the past and the loss of community
Article In this article, Mishra connects Simone Weil's concept of uprootedness to her own experiences moving to a Himalayan village. Uprootedness...
-

The New Age of Surveillance
Article In this article, the author discusses how the emergence of the Internet of Things is ushering in a new age...
-

The New Era of Corporate Censorship
Article This blog post discusses the situation of Cloudflare removing The Daily Stormer's account. The author argues that tech companies deciding what...
-

The Newly Reintroduced Phrack Issue 70
Article This article describes Phrack Magazine's comeback in 2021. Phrack Magazine is an online hacker magazine. This article describes how issues of...
-

The New Workplace: Where Meaning And Purpose Are More Important Than Ever
Article In this article, business consultant Renelle Darr outlines the components needed for your work environment to feel meaningful for your...
-

The Noncompete Clause Gets a Closer Look
Article In this article, Lauren Weber talks about Biden’s executive order which asks FTC to limit the use of agreements that keep workers...
-

The pandemic has crushed young people’s spirits
Article In this article, Thomas S. Hibbs claims that the pandemic has given rise to widespread dislocation in a number of ways....
-
The Perils of Meritocracy
Article In this article, Garber discusses meritocracy. It’s one of the most loved ideas in American life, but she argues that it should...
-

The Post-Meritocracy Manifesto
Article In this article, the author proposes a different set of values and principles in open source software development. Meritocracy is...
-

The Power of Habit
Book The description for this book is as follows: "In The Power of Habit, award-winning business reporter Charles Duhigg takes us to the...
-

The Problem with Work: Feminism, Marxism, Antiwork Politics, and Postwork Imaginaries
Book The description for this book is as follows: "In The Problem with Work, Kathi Weeks boldly challenges the presupposition that work,...
-

The Python Code of Conduct
Article In this article, the former director and vice chairman of the Python Software Foundation outlines a code of conduct for...
-

The Reality of Developer Burnout
Article In this article, Kenneth Reitz shares his experience of software developer burnout and outlines mechanisms he put in place to...
-

The Real White Fragility: Does the White Upper Class Feel Exhausted and Oppressed by Meritocracy?
Article In this article, the author examines the question: does the white upper class feel exhausted and oppressed by meritocracy?
-

There's an Automation Crisis Underway Right Now, It's Just Mostly Invisible
Article This article describes the results of a research study on workplace automation’s impact on the individual worker. While the study...
-

The Return of Anonymous
Article This article tells the story of the return of the hacking and activist group Anonymous. In 2012 Anonymous reached the height...
-

The Return of Work in Critical Theory: Self, Society, Politics
Book In this book, the authors explore what work is and why it is significant for us as people. They begin...
-

The Rise of the Meritocracy
The description for this book is as follows: "Michael Young has christened the oligarchy of the future "Meritocracy." Indeed, the...
-

The Rise of Workplace Surveillance
Podcast From the episode's notes: Across industries and income brackets, a growing number of American workers are discovering that their productivity...
-

These 6 tech companies have made the controversial decision to try to operate in China, where the government can demand social media posts be removed or search results be censored
Article This article outlines six different ways tech companies have censored content in order to operate in China amidst strict Chinese Internet...
-
The Secret History of Hacking
Video This video depicts some of the secret side of the history of hacking from black hat hackers to white hat hackers....
-

The Secret History of Women in Coding
Article In this article, Clive Thompson recounts the history of women in coding, looking at many different female pioneers in the field.
-

The Secretive Company That Might End Privacy as We Know It
Article This article discusses the controversial face recognition technology company Clearview AI. The article details how Clearview AI was founded, how...
-

The Semplica-Girl Diaries
Fiction In this short fiction piece, George Saunders writes diary entries from the perspective of a person living in a not-so-distant...
-

The shock and pain of cyber-bullying
Article This article describes how cyberbullying can affect a family from two different perspectives: first, from the perspective of the family who lost...
-

The Spectacular Rise and Fall of WeWork
Video In this video, Bloomberg Quicktake tells the story of the rise and fall of WeWork, a commercial office leasing company...
-

The Terrifying Power of Internet Censors
Article This article discusses the situation in which Cloudflare terminated The Daily Stormer's account. The author proposes that this event is a...
-

The Trolley Problem
Video In this video, BBC Radio 4 discusses the famous Trolley Problem. In this ethical thought experiment, you witness that a...
-
The Trolley, the Bull Bar, and Why Engineers Should Care About the Ethics of Autonomous Cars
Academic Paper This academic paper has the following abstract: "Everyone agrees that autonomous cars ought to save lives. Even if the cars do...
-

The Trolls Are Winning the Internet, Technologists Say
Article In this article, Adrienne LaFrance describes how Internet trolls shape discourse online. LaFrance notes that the current solutions will push...
-

The Tyranny of Merit
The description for this book is as follows: "The world-renowned philosopher and author of the bestselling Justice explores the central question of...
-

The Tyranny of Merit (Video)
Video In this video, Michael discusses what accounts for our polarized public life, and how we can begin to heal it....
-

The United States Isn't Doomed to Lose the Information Wars
Article In this article, Doowan Lee discusses the ways China and Russia have launched disinformation attacks online and suggests a few...
-

The US System for "Skilled" Migrants is Broken
Article In this article, the author provides an overview of the H1-B Visa, explains why it was created, and describes some...
-

The WeWork Documentary Explores a Decade of Delusion
Article In this article, Lizzie Widdicombe summarizes the documentary “WeWork: Or the Making and Breaking of a $47 Billion Unicorn." Widdicombe provides...
-

The WIRED Guide to Net Neutrality
Article This article provides a overview of the struggle to maintain net neutrality. Both the history of net neutrality and the future...
-

The Woke Meritocracy
Article In this article, the author discusses how telling the right stories about overcoming oppression in the right way became a...
-
The Woman Bringing Civility to Open Source Projects
Article In this article, Coraline Ada Ehmke is featured as "the woman bringing civility to open source projects". Ehmke is the principal...
-

The Work-Family Imbalance
Article In this article, Anand Iyer discusses the importance of prioritizing work-family life balance, especially for fathers. Iyer presents research that...
-

The World Needs Deepfake Experts to Stem This Chaos
Article This article describes a situation in Myanmar in which a political prisoner's confession video was accused as being a deepfake because...
-

‘The World’s Biggest Terrorist Has a Pikachu Bedspread’
Article This article tells the story of Reality Winner, an American Whistleblower who was sentenced for leaking a government report about Russian...
-
This researcher programmed bots to fight racism on Twitter. It worked.
Article In this article, Kevin Munger describes an experiment he performed on Twitter to attempt to discourage users from using harassing...
-

Thoughts on Network Neutrality, the FCC, and the Future of Internet Governance
Article In this blog post, Matthew Prince, the CEO of Cloudflare, shares his thoughts on FCC regulations that regulate Internet Service Providers....
-

Thus Spoke Zarathustra
Book The description for this book is as follows: "Nietzsche was one of the most revolutionary and subversive thinkers in Western...
-

To Be a Better Philanthropist, Think Like a Poker Player | Liv Boeree on Effective Altruism
Video In this video, Liv Boeree explains the effective altruism movement, which seeks to apply the scientific method to charitable giving...
-

To be of use
Poem In this poem, Marge Piercy glorifies work and workers. She claims that meaningful work is a natural desire of humans, and...
-

To catch a priest
Article In this article, the author speculates how cell phone data was used to demonstrate that Msgr. Jeffrey Burrill was using...
-
ToneLoc
Article This article from the textfiles website by two hackers with handles Minor Threat & Mucho Maas provide a user manual for the well...
-

Triumphs of Experience
Book The description from this book is as follows: "At a time when many people around the world are living into...
-

Trust the News? Lecture Slides
Lecture / slides In these lecture slides for the Ethical and Professional Issues course in Notre Dame's Computer Science and Engineering department, the following...
-

Twitter begins emailing the 677,775 Americans who took Russian election bait
Article This article details how Twitter emailed all users who interacted with accounts confirmed to be from the Russian troll farm that meddled...
-

Uber Video Shows the Kind of Crash Self-Driving Cars Are Made to Avoid
Article This article describes the video footage from an Uber-owned autonomous vehicle that hit and killed a pedestrian. From the video it...
-

Unauthorized Access
Video This video is a documentary about hackers by Annalisa Savage from 1994. From the video description, "This is a nostalgic hacker documentary...
-

Understanding Visual Memes: An Empirical Analysis of Text Superimposed on Memes Shared on Twitter
Academic Paper This academic paper has the following abstract: Visual memes have become an important mechanism through which ideologically potent and hateful...
-
Unix Use and Security From The Ground Up
Article This article written by the hacker The Prophet for textfiles.com about the security and uses of Unix. Hackers in the early 1990s would...
-

Unmasking Reddit's Violentacrez, The Biggest Troll on the Web
Article This article exposes the man behind the Reddit account Violentacrez. Up until this article was published, Violentacrez, a prominent Reddit...
-

U.S. House unanimously approves sweeping self-driving car measure
Article This article describes a unanimous approval by the US House of Representatives in 2017 to speed the deployment of self-driving cars...
-

Using Philosophy to Deal with a Mid-Career Crisis
Video In this video, philosophy professor Kieran Setiya discusses how he used philosophy to address a midlife crisis, which prompted him to...
-

US military must prepare for POW concerns in the deepfake era
Article This article describes the threat deepfakes present to prisoner of war situations. Previously, authoritarian regimes have tried to exploit American...
-

Utilitarianism: Crash Course Philosophy
Video In this video, get a crash course on Utilitarianism. Utilitarianism is the doctrine that actions are right if they are useful...
-

'Utterly horrifying': ex-Facebook insider says covert data harvesting was routine
Article In this article, we hear the concerns of Sandy Parakilas, a former Facebook employee who directly observed Facebook treating user...
-

UW professor: The information war is real, and we’re losing it
Article In this article, the author discusses Kate Starbird, a professor at the University of Washington, and her study of conspiracy theories...
-

Violent memes and messages surging on far-left social media, a new report finds
Article This article describes how memes incited violence on left-wing social media in the summer of 2020 after the killing of George...
-

Virtualized Horror Lecture Slides
Lecture / slides Slides for Lecture 16 of Ethical and Professional Issues in Notre Dame's Computer Science and Engineering department. The learning goals for...
-

Virtue and Technology (part 1) Lecture Slides
Lecture / slides In these lecture slides, the Virtue Ethics framework is introduced as a framework for evaluating ethical issues in technology. These...
-

Virtue and Technology (part 2) Lecture Slides
Lecture / slides In these lecture slides, Paul Blaschko and Sam Kennedy give a guest lecture to Walter Scheirer's Ethical and Professional Issues...
-

Visa Rejections for Tech Workers Spike Under Trump
Article In this article, the author assesses the impact of the stricter H-1B Visa policies enacted under former President Trump. The author follows...
-

Vita Activa and the Human Condition (Chapter 1)
Philosophical Text In the first chapter of her book The Human Condition, Hannah Arendt describes the "Vita Activa," or the active life...
-

Vita activa, the Spirit of Hannah Arendt (Trailer)
Video In this video, the IDFA (International Documentary Film Festival Amsterdam) provides a trailer for a documentary presented at IDFA 2015...
-

Wages Against Housework
Article In this short essay, Silvia Federici argues not only that women should receive wages for the housework they are expected to do, but...
-

Walter Scheirer Interviews Kevin Bowyer
Video In this video, Dr. Walter Scheirer Interviews facial recognition and biometrics expert Dr. Kevin Bowyer about the ethics of facial...
-

Walter Scheirer Interviews Kirsten Martin
Video In this video, Prof. Walter Scheirer (Computer Science, Notre Dame) interviews Dr. Kristen Martin, expert on technology ethics and privacy,...
-
Walter Scheirer Interviews Ron Metoyer
Video In this video, Prof. Walter Scheirer (Computer Science, University of Notre Dame) interviews Dr. Ron Metoyer, Professor of Computer Science...
-

Want To Find Your Purpose At Work? Change Your Perceptions
Book In this article, Tracy Bower argues that the way in which you think about your work is critical to finding fulfillment....
-
War Dialer
Digital Artifact This article provides historical context and the technical developments in wardialing and war dialers. War dialing is a technique developed by hackers...
-

Warez: The Infrastructure and Aesthetics of Piracy
Book This book is written by Martin Paul Eve, a Professor of Literature, Technology and Publishing, about the Warez Scene and community. This...
-
Watch Me Demo My New IRC Client on an 80s Retro Computer
Video This video is a video of a demo of Internet Relay Chat (IRC) on an 80s retro computer. The IRC is highly...
-

We Are Legion - The Story of the Hacktivists
Video In this video clip from the documentary "We Are Legion," 4Chan's influence on Internet culture and trolling is described. The impact...
-

We Are Legion The Story of the Hacktivists
Video This video is a documentary directed by Brian Knappenberger that gives a detailed look at the beginnings of hacktivist group `Anonymous', and how they...
-

Wearing Many Hats: The Rise of the Professional Security Hacker
Article This article in Data & Society is a discussion with Matt Goerzen and Gabriella Coleman about the evolving culture around exploits development....
-

We desperately need a way to defend against online propaganda
Article This article describes how fake news spreads on social media, why "not feeding the trolls" isn't a sufficient solution, and why...
-

‘We Got To Be Cool About This‘: An Oral History of the L0pht, Part 1
Article This article provides an overview of how the influential hacking group L0pht formed in the 90s. The article tells the story...
-

We Hire the Best, Just Like Everyone Else
Article In this article, Jeff Atwood is skeptical about hiring the "best" people and advocates for different approaches.
-

Welcome to the Age of Privacy Nihilism
Article In this article, Ian Bogost provides an overview of the history of business intelligence. While the uncannily-appropriate nature of the targeted...
-

We only hire the trendiest
Article In this article, Dan Luu discusses the pitfalls of only hiring the "trendiest" people.
-
Were You Asked to Sign a Non-compete Agreement? Watch this first!
Article In this video, Michigan Ross Professor Norm Bishara shows you five simple steps to take before, and after, you sign...
-

We tried the AI software companies like Goldman Sachs and Unilever use to analyze job applicants
Video In this video, Business Insider explores HireVue, a new AI technology for screening job applicants. The video explains how HireVue...
-

What Do Programmers Care About?
Video In this video, Joel Spolsky from Stack Overflow speaks on 'What do top programmers really care about when looking for...
-

What Happens When Employers Can Read Your Facial Expressions?
Article This article outlines the risks of facial recognition technology. The authors outline three arguments that those against facial recognition technology...
-
What happens when we work non-stop
Article In this article, José Luis Peñarredonda discusses the experience of overworked workers, despite overwhelming evidence that working a healthy number of hours increases...
-

What is a Hacker?
Video This video is produced by The Media Show and has Mitch Altman as a guest to answer the question: What is a...
-

What is an H-1B Visa?
Video This video explains what an H-1B Visa is, its history, and critical opinions of H1-B visas.
-

What is Burnout?
Video In this video, Dr. Larissa Thomas, focusing mostly on physicians, covers the three main elements of burnout: emotional exhaustion, cynicism...
-

What is Ethics?
From the video description: Ethics asks how we should live, what choices we should make and what makes our lives...
-

What is the difference between Ethics, Morality and the Law?
Video In this video, three different categories of demands on how we should live - ethics, morality, and law - are...
-

What Liberals Get Wrong About Work
Article In this article, Sandel argues that the American meritocratic mythos, lack of legal protections or recognition for manual laborers, and stagnated...
-

What Money Can't Buy
Book The description for this book is as follows: "In What Money Can't Buy, renowned political philosopher Michael J. Sandel rethinks the role...
-

What Work is Really For
Article In this essay, Professor Gary Gutting (who taught at the University of Notre Dame until 2019) approaches the question of...
-
Whence and W(h)ither Technology Ethics
Book The Oxford Handbook of Philosophy of Technology gives readers a view into this increasingly vital and urgently needed domain of...
-

Where Do I Want To Work? Lecture Slides
Lecture / slides In these lecture slides from the Ethical and Professional Issues course in the Computer Science and Engineering department at Notre Dame,...
-
Who controls the Internet?
Article In this article, it attempts to answer the question "Who owns the internet". Decentralization means the Internet is controlled by...
-

Who Spewed That Abuse? Anonymous Yik Yak App Isn’t Telling
Article This article discusses the social media app Yik Yak. The article discusses how Yik Yak was founded on the principles of...
-

Who Watches the Watchers? Lecture Slides
Lecture / slides Slides for Lecture 23 of Ethical and Professional Issues in Notre Dame's Computer Science and Engineering department. In this lecture,...
-

Why Are Young People Pretending to Love Work
Article In this article, Griffith explores the phenomenon of "workaholism" in younger generations. She argues that this culture benefits those in...
-

Why Cloudflare Let an Extremist Stronghold Burn
Article This article highlights one example of the tricky balance between allowing free speech on the Internet while mitigating hateful content. Cloudflare...
-

Why Doesn’t Silicon Valley Hire Black Coders?
Article In this article, Vauhini Vara addresses the lack of representation of black coders at Google and why this occurs, looking specifically at...
-

Why Edward Snowden Is a Hero
Article In this article, the author expresses their opinion on why Edward Snowden is a hero. The article describes what Snowden's...
-

Why Facebook is losing the war on hate speech in Myanmar
Article In this article, Steve Secklow investigates why Facebook is failing to curb the spread of hate speech against ethnic minorities...
-

Why hiring the ‘best’ people produces the least creative results
Article In this article, Dr. Page argues that hiring the "best" people produces the least creative results.
-

Why I Put My Wife's Career First
Article In this article, Andrew Moravcsik, husband of Anne-Marie Slaughter (who wrote this article about working mothers) describes his experience as a...
-

Why is hiring broken? It starts at the whiteboard.
Article In this article, open source extraordinaire Sahat Yalkabov explains why he has given up his search for a front end...
-

Why Is Work so Boring?
Video In this video, the School of Life argues that many people find work boring because they are forced to specialize....
-

Why It Pays to Work Hard: Ted Talk
Video In this video, Richard St. John proposes a simple shift in attitude to turn mediocre into incredible. Nothing comes easy, and...
-

Why It's OK to Want to Be Rich
Book From the book description: "Finger-wagging moralizers say the love of money is the root of all evil. They assume that...
-

Why Millennials Are Leaving Six-Figure Tech Jobs
Video From the video description: "Tech jobs are known to have some of the most lavish benefits and perks, not to...
-

Why Recent Grads Don't Negotiate
Article In this article, Ross explores the reasons why recent grads choose not to negotiate job offers and why this may not be...
-

Why Silicon Valley is Embracing Universal Basic Income
Article This article describes how Universal Basic Income (UBI) works, and how it fits into Silicon Valley’s agenda. While some critics...
-
Why Software is Eating the World
Article In this article, Marc Andreessen argues that the rapid growth of tech companies will not lead to a dangerous new...
-

Why Tech Is the Leading Industry on Parental Leave
Article In this article, Bourree Lam profiles Etsy's updated parental leave policy from 12 weeks to 26 weeks. Lam cites two main...
-
Why Tech Leadership Has a Bigger Race Than Gender Problem
Article In this article, the findings of a new study from Ascend Leadership that there may be an overrepresentation of Asians in tech—but...
-

Why the Future Doesn't Need Us
Article From the article summary: "Bill Joy, cofounder and and chief scientist of Sun Microsystems, argues that the technologies of the future...
-
Why the Open Code of Conduct Isn't For Me
Article In this article, the author shares his opinion on GitHub’s new Open Code of Conduct. Specifically, the author critiques the...
-

Why the STEM gender gap is overblown
Article In this article, Denise Cummins explains that although women are just as capable of performing in STEM fields as men, this...
-

Why The U.S. Government And Big Tech Disagree On Encryption
Video This video has the following description: Encryption takes data like a text message or email and converts it into code to...
-

Why Using an Ad Blocker Is Stealing
Article In this article, the author discusses why using an ad blocker is stealing. The author argues that using an ad...
-

Why Women Don't Code
Article In this article, Stuart Reges discusses his opinion on why men and women are "different" and why these "differences" are responsible...
-

Why Women Don’t Negotiate Their Job Offers
Article In this article, the legitimate reasons women don't negotiate their salaries and how they can negotiate without a "social cost".
-

Why Women Still Can't Have It All
Article In this article, Anne-Marie Slaughter draws from her own professional experience to explain why it is incredibly hard for women...
-

Why You Should Embrace Surveillance, Not Fight It
Article From the article description: "The internet is a tracking and monitoring machine. We will ceaselessly self-track and be tracked. We’re expanding...
-

Why You Should Stop Trying to Be Happy at Work
Article Article summary written by the author: "What are we really searching for when we say we want more “meaning” at...
-

Women’s unpaid work must be included in GDP calculations: lessons from history
Article In this article, Luke Messac argues that unpaid houshold labor should be included in calculations of GDP. Gross Domestic Product is a...
-

WORK AND EMANCIPATORY PRACTICE: TOWARDS A RECOVERY OF HUMAN BEINGS’ PRODUCTIVE CAPACITIES
Other The abstract for this paper is as follows: This article argues that productive work represents a mode of human flourishing...
-

Work and the Good Life Method (Selections from "Nicomachean Ethics")
Philosophical Text In these excerpts from Aristotle's Nicomachean Ethics, he discusses what it takes to live a good life. Aristotle argues that, like...
-

Working: People Talk About What They Do All Day and How They Feel About What They Do
Book The description for this book is as follows: "Perhaps Studs Terkel’s best-known book, Working is a compelling, fascinating look at jobs and...
-

Workism is Making Americans Miserable
Article In this article, Derek Thompson outlines the new "workism" phenomenon. Despite predictions from 20th century intellectuals that Americans in the...
-

Work-Life Balance
Video In this video, The School of Life explains why work-life balance is impossible. They argue that our brains are generalists,...
-

Writing Reflection 00: Ethical Frameworks
Writing Reflection The first writing reflection assignment for Ethical and Professional Issues in Notre Dame's Computer Science and Engineering department. The assignment asks...
-

Writing Reflection 01: Jobs in the Tech Industry
Writing Reflection The second writing assignment for Ethical and Professional Issues in Notre Dame's Computer Science and Engineering department. The assignment asks...
-

Writing Reflection 02: What does success look like?
Writing Reflection In this writing reflection, students in Ethical and Professional Issues (in Notre Dame's Computer Science and Engineering department) are encouraged...
-

Writing Reflection 03: Valuable Time and Good People
Writing Reflection In this writing reflection from the Ethical and Professional Issues course in Notre Dame's Computer Science and Engineering department, the students are encouraged...
-

Writing Reflection 04: Social Media and the Internet
Writing Reflection In this writing reflection, students in the Ethical and Professional Issues course in Notre Dame's Computer Science and Engineering department...
-

Writing Reflection 05: Exposure of Anonymity?
Writing Reflection In this writing reflection for the Ethical and Professional Issues course in Notre Dame's Computer Science and Engineering department, students are...
-

Writing Reflection 06: The Very Weird Internet
Writing Reflection In this writing reflection, students in the Ethical and Professional Issues course in Notre Dame's Computer Science and Engineering department...
-

Writing Reflection 07: You've Been Canceled!
Writing Reflection The eighth writing reflection for Ethical and Professional Issues in Notre Dame's Computer Science and Engineering department. The writing reflection encourages...
-

Writing Reflection 08: Artificial Perception
Writing Reflection The ninth writing assignment for Ethical and Professional Issues in Notre Dame's Computer Science and Engineering department.This assignment encourages students to...
-

Writing Reflection 09: Face the Facts of AI
Writing Reflection The tenth writing reflection for Ethical and Professional Issues in Notre Dame's Computer Science and Engineering department. This assignment asks...
-

Writing Reflection 10: Hackers and Leakers
Writing Reflection In this writing assignment for Ethical and Professional Issues in Notre Dame's Computer Science and Engineering department, students are asked...
-

Xbox's new Code of Conduct: yes to "get wrecked," "potato aim," no to hate
Article In this article the author discusses Xbox's Code of Conduct, and in particular discusses Xbox's distinction between trash talk (acceptable) and harassment...
-

You Must Change Your Life
Article In this article, Hari Kunzru explains how the phenonemon of "executive athleticism" coupled with the remote working environment has caused tremendous amounts of...
-

Young Chinese Bemoan Rat Race With Tongue-in-Cheek Memes
Article This article describes Chinese memes about the country’s work culture that surfaced during the bleak job market of the COVID-19...
-

Your Interview With AI
Article This article discusses HireVue, an AI-based job hiring platform. The article discusses the ethical concerns surrounding HireVue and HireVue's responses to...
-

You Should Plan On Switching Jobs Every Three Years For The Rest Of Your Life
Article In this article, Vivian Giang discusses why the stigma of being a flaky job-hopper is quickly becoming a thing of the...
-

You Won't Believe What Obama Says In This Video!
Video In this video, it appears as if Former President Barack Obama is delivering an important message. However, as the video...