Technology
-

Advanced Network Reconnaissance with Nmap
Video This video is a presentation by Gordoon Lyon aka Fydor, the creator of the nmap network scanner, from ShmooCon 2006. From...
-
A Novice's Guide to Hacking- 1989 edition
Article This article is a classic piece of self-directed training in hacking by a hacker with the handle The Mentor from the...
-

Apple I
Digital Artifact This article details the technical development and contextual history of the Apple I, originally released under the name Apple Computer. This...
-
A Prehistory of Social Media
Article This article provides an introduction to the birth of social media by providing a "prehistory" of the internet itself. The article focuses...
-

Archaeology of Hacking: Textfiles Explainer
Video This video an overview of the hacker underground media sharing platform known as textfiles.
-

Back Orifice
Digital Artifact This article details the digital artifact Back Orifice (a play on Windows Back Office) created by the hacking group Cult of the...
-

BBS The Documentary: Episode 1 of 8: BAUD (The Beginning)
Video This video is episode 1 of 8 of a documentary mini-series by Jason Scott about the bulletin board systems (BBS). From...
-

Book Launch: The Hacker and the State
Video This video is the book launch of Dr. Ben Buchanan's book The Hacker and the State. From the video description, "Packed with...
-
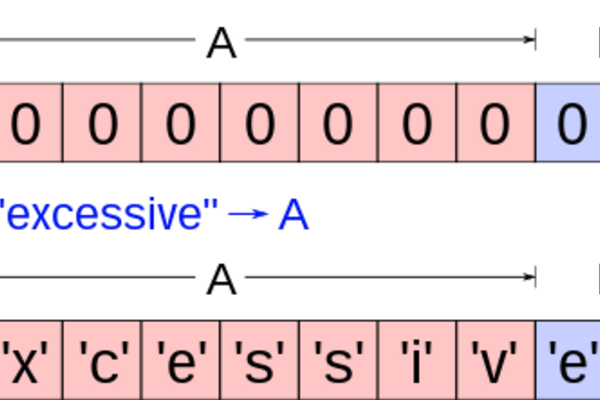
Buffer Overflow Exploit
Digital Artifact This article describes the digital artifact of a buffer overflow exploit. A buffer overflow is an anomaly where a program writes...
-
CONFidence 2021: The Coming AI Hackers
Video This video is from CONfidence 2021 from Bruce Schneier discussing the future of hacking. From the video description, "Hacking is a human endeavor,...
-

Crypto
Book Chapter This book chapter is from Steven Levy's book "Crypto" which tells the stories of key figures behind cryptography and the cypherpunk movement. This...
-

Cult of the Dead Cow
Book Chapter This book chapter from the recent book on the hacking group the Cult of the Dead Cow is about the Back Orifice...
-

Darknet Diaries Ep: 45 Xbox Underground
Video This video details one of the biggest hacks on the Xbox gaming console. From the video description, "It started as a...
-

DEF CON 19 - Jason Scott - Archive Team: A Distributed Preservation of Service Attack
Video This video depicts a presentation by Jason Scott at the hacker conference, DEFCON '19 about the preservation of digital artifacts on...
-

Digital Archaeology: Rescuing Neglected and Damaged Data Resources
Academic Paper This article from the University of Glasgow is a handy guide for historical preservation in the 1990s that makes use of...
-

Digital Equipment Corporation PDP-11
Digital Artifact This article details the history and technical developments of the PDP-11, a series of 16-bit microcomputers sold by Digital Equipment Corporation...
-

Exploding the Phone
Book This book provides an in-depth historical perspective and study of phone phreaking and hackers of the telecommunication industry known as phone...
-

Good Work
Book The description for this book is as follows: "What does it mean to carry out "good work"? What strategies allow...
-

H2K2: The Conscience of a Hacker
Video This video is of the hacker who goes by the handle The Mentor reading his famous essay from 1986, titled "The...
-

Hackers: Heroes of the Computer Revolution
Book Steven Levy's book is is a classic text on the history of computing. It is used throughout the course to highlight the hacker...
-

Hackers Testimony at the United States Senate
Video This video depicts the testimony of the hacker group, L0pht Heavy Industries, in front of the United States Senate in 1998. The...
-

Hackers - Wizards of the Electronic Age
Video This video is a short documentary about the hacker underground and the foundations of the hacker ethic. From the video description,...
-
Hacking at the Crossroad: U.S. Military Funding of Hackerspaces
Article This article is an influential piece written by the inventor Mitch Altman about the influence of defense funding in technological development. It...
-
History of Gnu, Linux, Free and Open Software
Video This video depicts the history of the open source and free software movements including the history and technological development of Gnu and...
-

How the Apple-1 Works
Video This video provides a technical overview of the Apple-1 Computer. The technical aspects of the computer are described and shown as...
-

Inventing Copyleft
Article This book chapter is from Christopher Kelty's book called "Two Bits: The Cultural Significance of Free Software" that details the history of Free...
-

Linux Operating System
Digital Artifact This article describes the digital artifact of the Linux Operating System which is a family of open-source Unix-like operating systems based on...
-
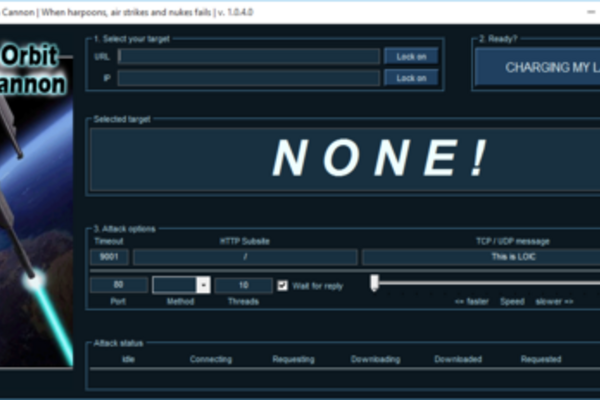
Low Orbit Ion Cannon
Digital Artifact This article describes the digital artifact Low Orbit Ion Cannon which was originally created by Praetox Technologies. The Low Orbit Ion Cannon...
-

Masters of Crowds: The Rise of Mass Social Engineering
Article This article provides a deep history of mass manipulation from the 1920s through the mid-1970s. This article is adapted from the...
-
Nessus Proprietary Security Scanner.
Digital Artifact This technology is a digital artifact by Tenable which is the Nessus Properitary Security Scanner. This technology is properitary software from...
-

Network Mapper (nmap)
Digital Artifact This article presents the Network Mapper (nmap) tool created by Gordon Lyon who is also known by the psuedonym Fyodor Vaskovich. This tool...
-
.nfo File
Digital Artifact This article describes a digital artifact known as the .nfo file extension which is a shortening of info or information. This...
-
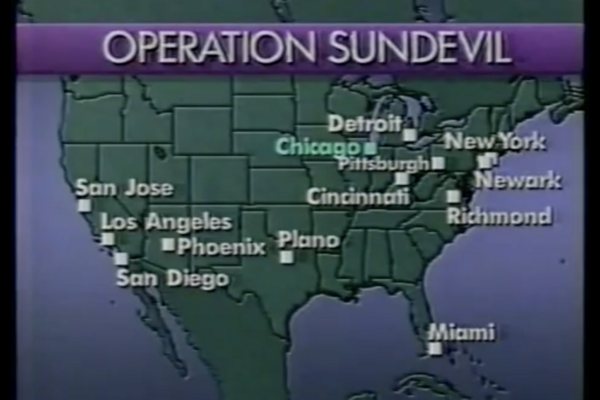
Operation Sundevil
Video The video provides a brief overview of Operation Sundevil from the 1990s. The operation was apart of a large hacker crackdown...
-

Phone Phreaking: A Call From Joybubbles
Video This video depicts a phone phreaking call made by the hacker Joybubbles aka Josef Engressia, Jr. This original sound byte comes...
-

Phrack Magazine - Issue 31
Article This article is an introduction to Issue 31 of the popular underground hacking publication of Phrack Magazine. This particular article details...
-

Red Box (Phreaking)
Article This article provides a technical description and history of the red box phone phreaking device. This device was created and utilized...
-

Remote OS detection via TCP/IP Stack FingerPrinting
Article This article is from issuse 54 of Phrack Magazine in 1998 written by Gordon Lyon aka Fydor, the creator of the...
-

Rene Carmille
Article This article details the life of Rene Carmille who is known to be one of the first hackers. This article gives a...
-

Representing Hacker Culture: Reading Phrack
Book Chapter This book chapter from Douglas Thomas' book Hacker Culture details an outsider's guide to reading the hacker zine Phrack. This chapter discusses...
-

Resistance to the current: the dialectics of hacking
Book Chapter This book chapter is titled "Internet Relay Chat: A Time Machine That Stood the Test of Time" and details the history...
-

Smashing the Stack for Fun and Profit
Article This article is from issue 49 of Phrack Magazine written by Elias Levy who also goes by the handle Aleph One in...
-
Social Engineering A Way of Life
Article This article is written by the hacker Malefactor [OC] in textfiles.com which provides a guide to hackers and phreaks on social...
-
Spacewar!
Digital Artifact This game is a digital artifact of a Javascript version of the popular Spacewar! video game that is one of the...
-
Stalking the Wily Hacker
Article This article tells the story of a hacker who penetrated Lawrence Berkeley National Laboratory in the 1980s. It provides an anecdotal perspective...
-

Storage Media
Article This article provides the technical developments of various data storage methods and mediums throughout history. These digital artifacts provide an understanding...
-
Stuxnet Worm
Digital Artifact This article describes the history and technological development of the Stuxnet Worm. The Stuxnet Worm is a malicious computer worm that was...
-

The Age of AI Hacking Is Closer Than You Think
This article is adapted from A Hacker’s Mind: How the Powerful Bend Society’s Rules, and How to Bend Them Back, by Bruce...
-

The Art of Deception
Book This book is a digital artifact used in the course to represent the area of social engineering. The book details several...
-

The Art of Port Scanning
Article This article from issue 51 of Phrack Magazine is written by Gordon Lyon aka Fydor about the nmap network scanner. This article introduced...
-

The First Hacker
Video This video gives an overview of Rene Carmille's contribution as the first hacker. From the video description: "Based on the extraordinary...
-

The Hackerspace Movement
Video This video is a Ted Talk given by Mitch Altman, the inventor and creator of the TV-B-Gone technology and famous hardware hacker....
-

The incredibly intricate badges of Def Con
Article This article details the creative badges created by hackers for their yearly hacking conference called DefCon. This article specifically details the...
-
The Secret History of Hacking
Video This video depicts some of the secret side of the history of hacking from black hat hackers to white hat hackers....
-
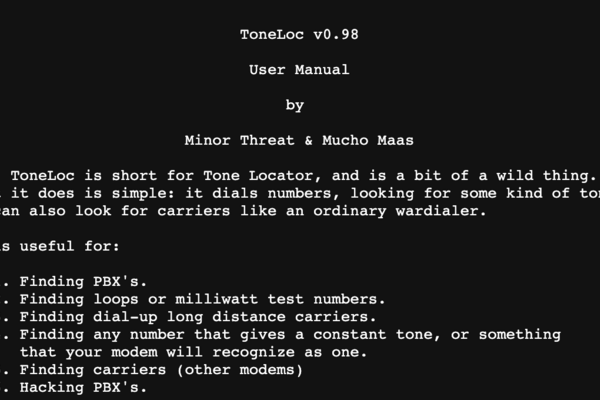
ToneLoc
Article This article from the textfiles website by two hackers with handles Minor Threat & Mucho Maas provide a user manual for the well...
-
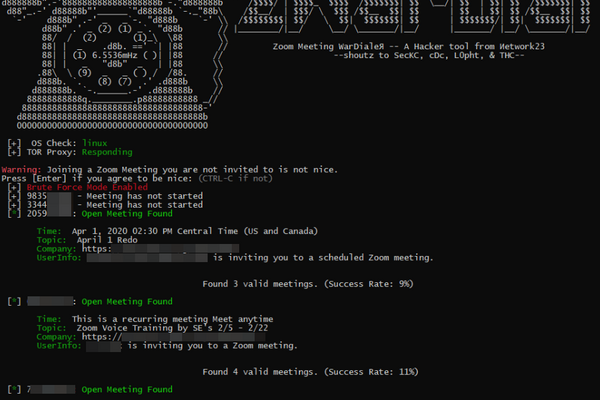
War Dialer
Digital Artifact This article provides historical context and the technical developments in wardialing and war dialers. War dialing is a technique developed by hackers...
-

Warez: The Infrastructure and Aesthetics of Piracy
Book This book is written by Martin Paul Eve, a Professor of Literature, Technology and Publishing, about the Warez Scene and community. This...
-
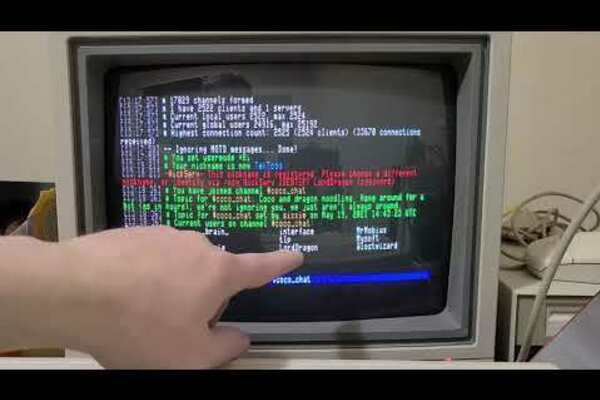
Watch Me Demo My New IRC Client on an 80s Retro Computer
Video This video is a video of a demo of Internet Relay Chat (IRC) on an 80s retro computer. The IRC is highly...
-

We Are Legion The Story of the Hacktivists
Video This video is a documentary directed by Brian Knappenberger that gives a detailed look at the beginnings of hacktivist group `Anonymous', and how they...
-

What is a Hacker?
Video This video is produced by The Media Show and has Mitch Altman as a guest to answer the question: What is a...